Phishing with hacked sites
SecureList
AUGUST 14, 2023
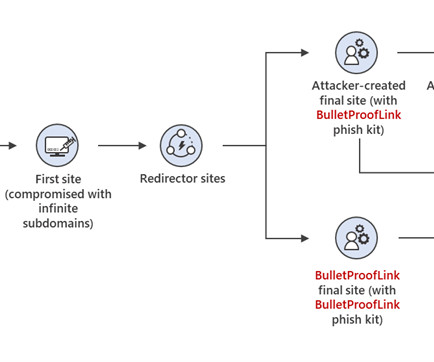
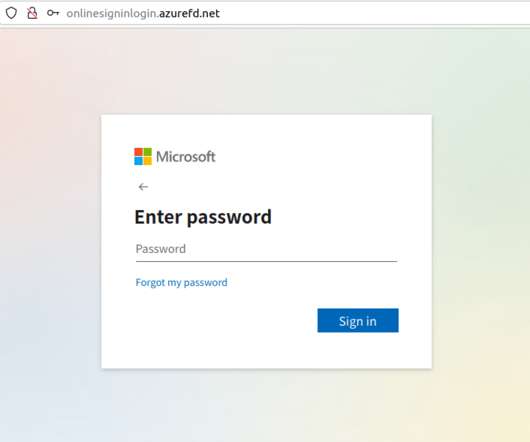
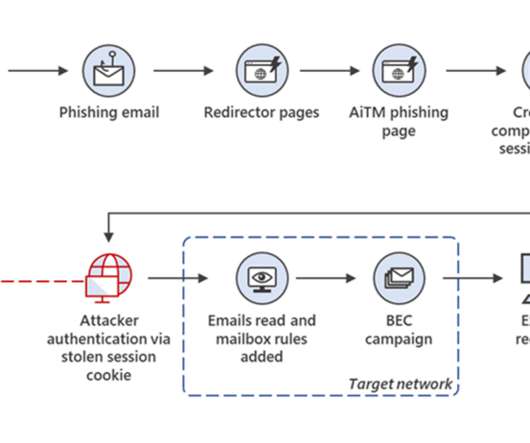
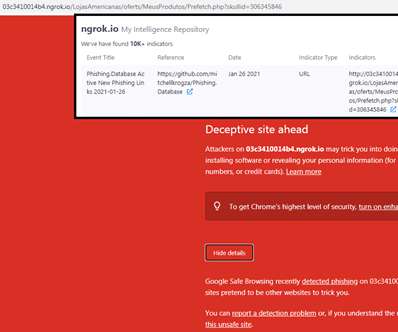
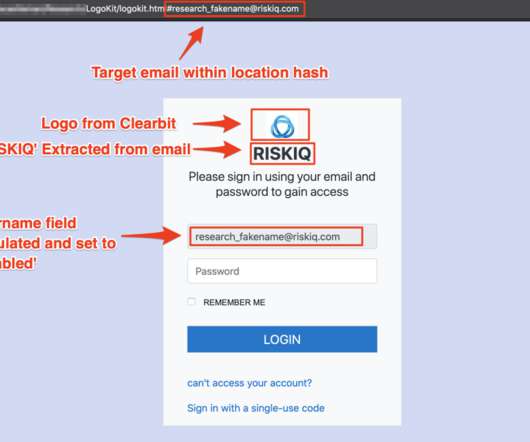
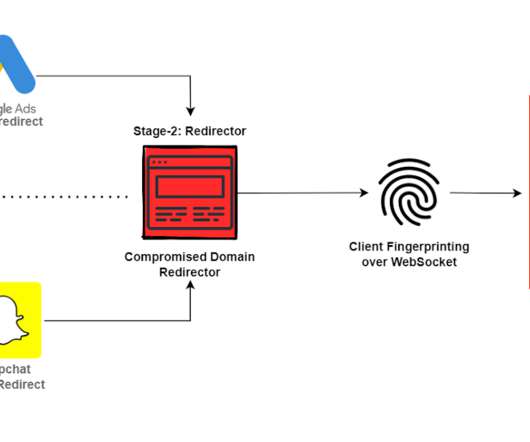
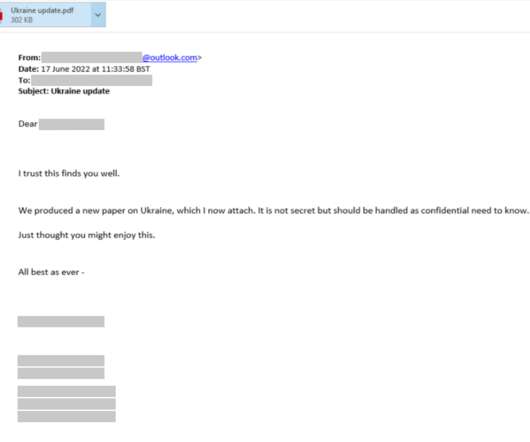
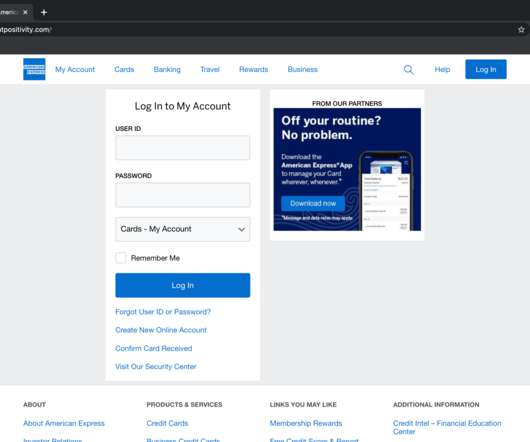
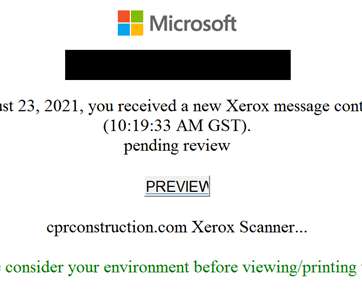
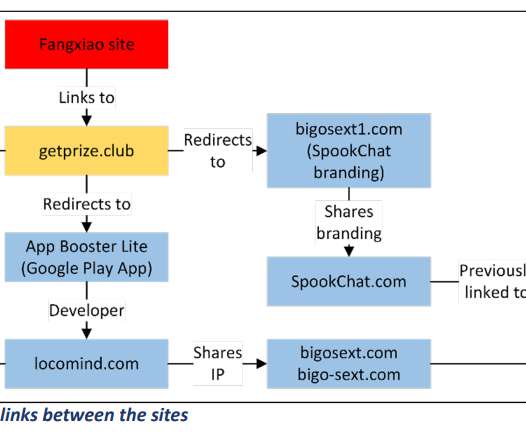
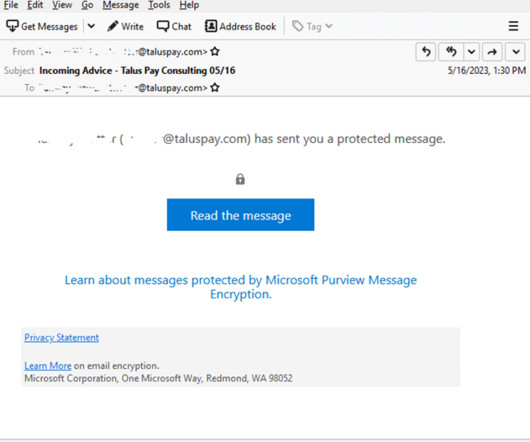
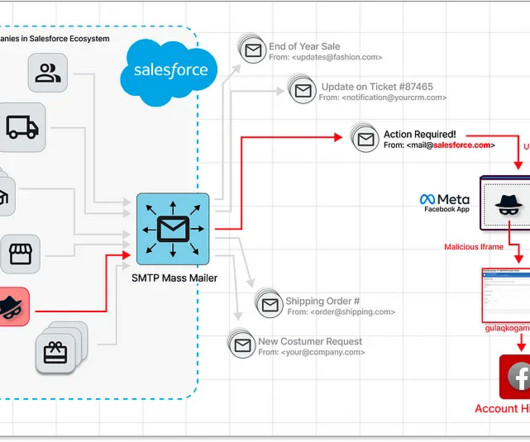
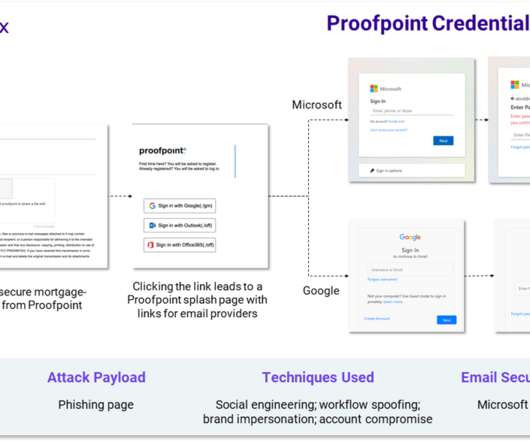
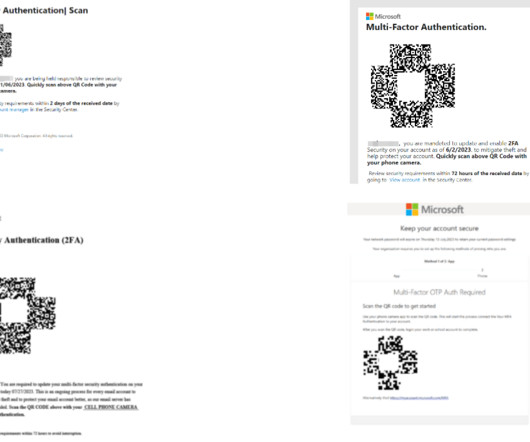
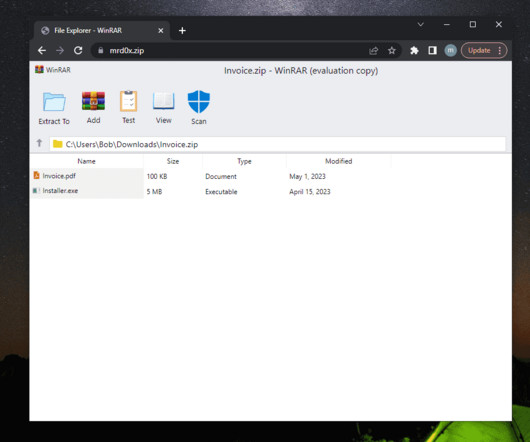
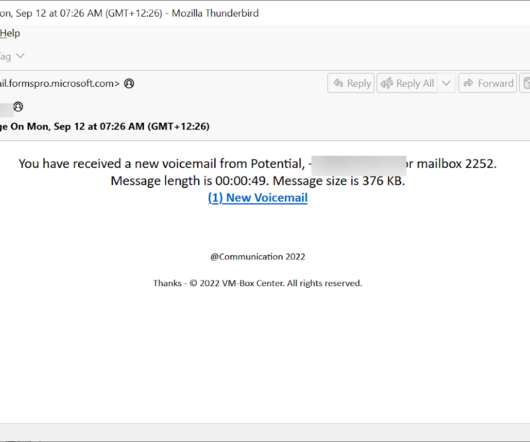
Examples include automation with phishing kits or Telegram bots. Another tactic, popular with scammers big and small, phishers included, is hacking websites and placing malicious content on those, rather than registering new domains. What sites get hacked the most Abandoned websites end up captured by cybercriminals fairly often.









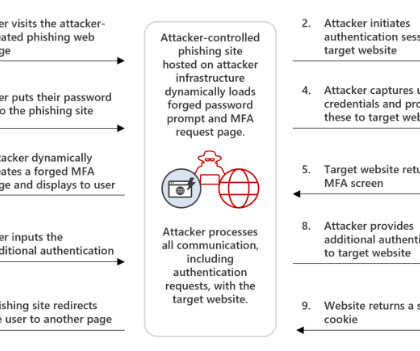
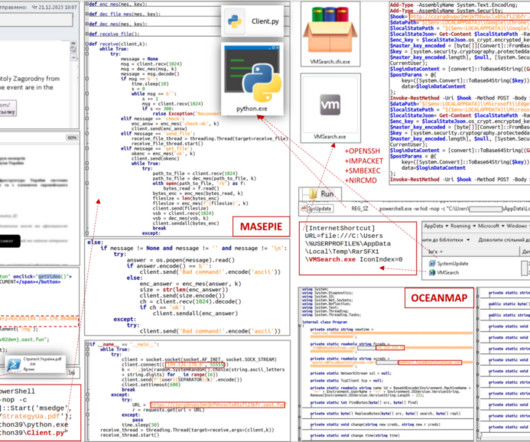


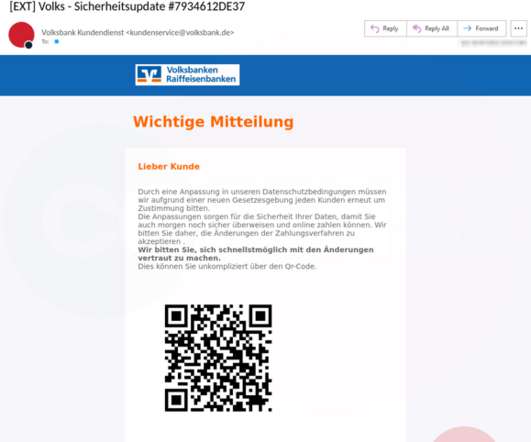












Let's personalize your content