Apple Guidance on Intimate Partner Surveillance
Adam Shostack
MAY 6, 2021
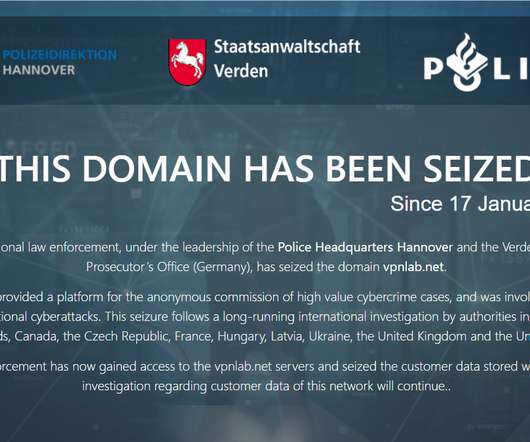
What you share, and whom you share it with, is up to you — including the decision to make changes to better protect your information or personal safety. Defending against attackers who are both authorized and “interface-bound” is a weird problem for information security, as traditionally defined.






















Let's personalize your content