Travel Update! The NIST CSF 2.0 is HERE…Along with Many Helpful Resources…
NSTIC
FEBRUARY 26, 2024
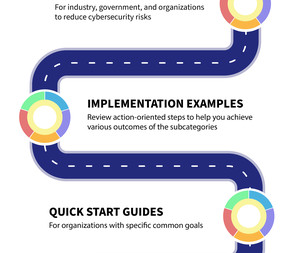
Informative References Cybersecurity & Privacy Reference Tool (CPRT) CSF 2.0 Reference Tool CSF 2.0 NIST CSF 2.0 QUICK LINKS | Explore our Full Suite of Resources: CSF 2.0 Quick Start Guides CSF 2.0 Profiles CSF 2.0







































Let's personalize your content