Spyware: What It Is, How It Works, and How to Prevent It
Security Boulevard
AUGUST 5, 2021
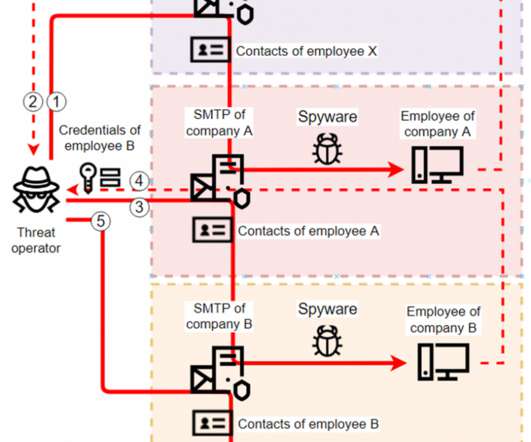
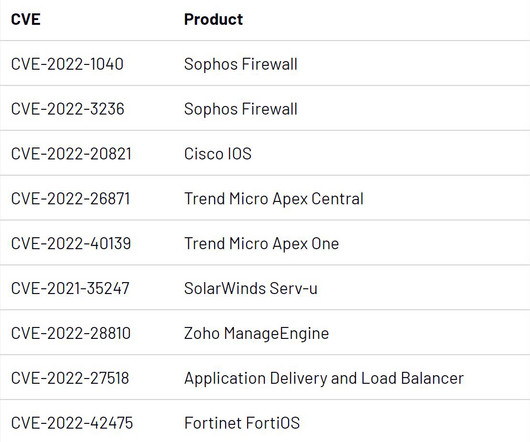
That culprit could be spyware. Spyware is software that tracks your internet surfing and [.]. The post Spyware: What It Is, How It Works, and How to Prevent It appeared first on TechSpective. The post Spyware: What It Is, How It Works, and How to Prevent It appeared first on Security Boulevard.



































Let's personalize your content