A Clear and Present Need: Bolster Your Identity Security with Threat Detection and Response
Duo's Security Blog
NOVEMBER 20, 2023
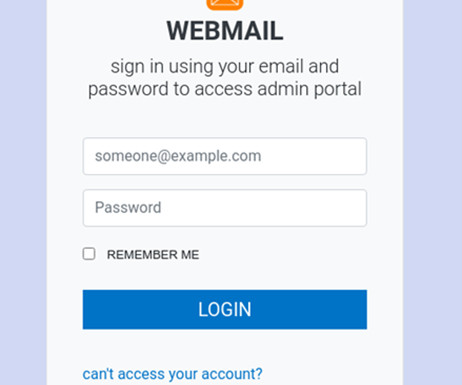
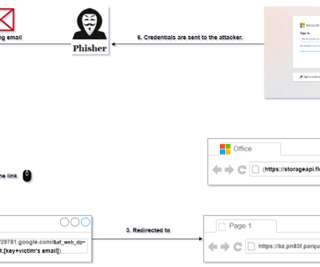
Security professionals agree that passwords are low hanging fruit for cybercriminals and can even be the keys to the kingdom when the compromised passwords belong to privileged accounts. According to a 2023 Cisco Duo sponsored survey , only 62% of organizations make MFA mandatory for their entire workforce.















































Let's personalize your content