Passwords Security: Past, Present, and Future
Security Boulevard
JULY 16, 2021
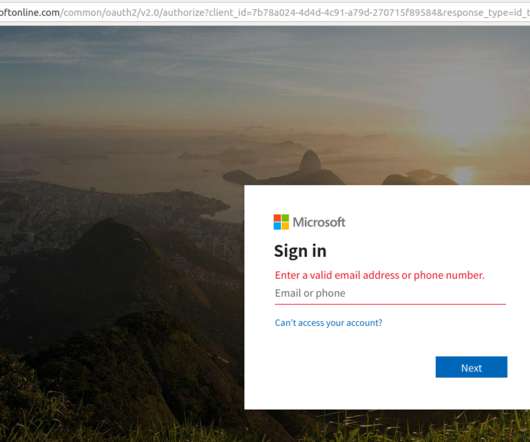
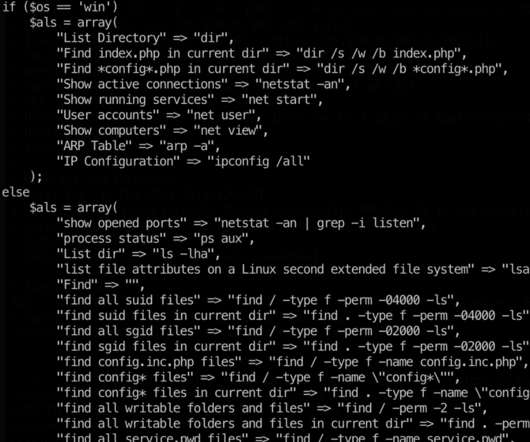
The recent report on The State Password Security in the Enterprise reveals several essential findings for system administrators and security professionals alike. First, whether we are happy about it or not, passwords are going to be around for a long time. And third, due to the frequency of cyber-attacks involving.

































Let's personalize your content