Apple Warns Users of Targeted Spyware Attacks – Here’s How to Stay Safe
Penetration Testing
APRIL 11, 2024
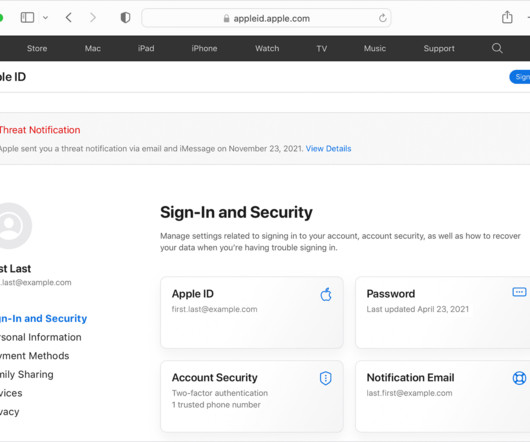
Apple has sent warnings to a growing number of users, alerting them about highly sophisticated mercenary spyware attacks.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Penetration Testing
APRIL 11, 2024
Apple has sent warnings to a growing number of users, alerting them about highly sophisticated mercenary spyware attacks.

Penetration Testing
JUNE 23, 2025
The post Wedding Invitation Scam: SpyMax RAT Targets Indian WhatsApp Users, Stealing OTPs & Banking Credentials appeared first on Daily CyberSecurity.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Malwarebytes
SEPTEMBER 4, 2024
After using passwords obtained from one of the countless breaches as a lure to trick victims into paying, the “Hello pervert” sextortion scammers have recently introduced two new pressure tactics: Name-dropping the infamous Pegasus spyware and adding pictures of your home environment. Scammers do this to bypass phishing filters.

Security Affairs
APRIL 9, 2020
Group-IB’s CERT-GIB analyzed hundreds of coronavirus -related phishing emails and discovered top malware strains in COVID-19 campaigns. Group-IB’s Computer Emergency Response Team ( CERT-GIB ) analyzed hundreds of coronavirus-related phishing emails between February 13 and April 1, 2020. Spyware: the most likely COVID-19 payload.

Malwarebytes
FEBRUARY 16, 2021
When COVID-19 cases first began spiking in several countries, cybercriminals preyed upon people’s fears mercilessly, with an avalanche of coronavirus phishing emails and scams. And as people adapted to their “new normal,” scammers exploited their isolation with a resurgence in tech support scams.

Webroot
FEBRUARY 21, 2025
Phishing scams, ransomware attacks, data breaches, and identity theft are part of a growing list of online dangers that are a daily reality. It combines multiple security capabilities into one easy-to-use package that includes: Antivirus protection Detects and neutralizes viruses, malware , spyware , and ransomware.

Security Affairs
NOVEMBER 17, 2024
CISA adds Palo Alto Networks Expedition bugs to its Known Exploited Vulnerabilities catalog Hackers target critical flaw CVE-2024-10914 in EOL D-Link NAS Devices China-linked threat actors compromised multiple telecos and spied on a limited number of U.S.

SecureList
MAY 3, 2021
Banking phishing: new version of an old scheme. In Q1 2021, new banking scams appeared alongside ones that are more traditional. Clients of several Dutch banks faced a phishing attack using QR codes. The link redirected them to a phishing page requesting their Microsoft account credentials. Quarterly highlights.

Security Affairs
FEBRUARY 9, 2025
What are the risks? US Justice Department says cybercrime forum allegedly affected 17 million Americans Cybercrime is increasingly complex.

Security Affairs
FEBRUARY 23, 2025
CISA adds SonicWall SonicOS and Palo Alto PAN-OS flaws to its Known Exploited Vulnerabilities catalog Juniper Networks fixed a critical flaw in Session Smart Routers China-linked APT group Winnti targets Japanese organizations since March 2024 Xerox VersaLink C7025 Multifunction printer flaws may expose Windows Active Directory credentials to attackers (..)

eSecurity Planet
NOVEMBER 12, 2024
Even McAfee’s most basic plan includes a VPN, identity monitoring, and text scam detection. Norton 360 lacks text scam detection, but again, Norton does offer a free detection tool, Genie. Norton doesn’t have spyware protection; I recommend looking at business antivirus products if that’s a priority for you. 5 Pricing: 4.7/5

Hacker's King
MAY 24, 2025
In simpler terms, phishing scams, brute force attacks, and MFA bypass techniques. Phishing attacks Phishing so far makes for the most dangerous aspect of cybersecurity. Unlike the traditional methods of sending more information about a certain service, a phishing email acts the complete opposite.

Security Boulevard
MARCH 24, 2025
Researchers name several countries as potential Paragon spyware customers TechCrunch The Citizen Lab, a group of academics and security researchers, recently published a report indicating the governments of Australia, Canada, Cyprus, Denmark, Israel, and Singapore are "likely" customers of Israeli spyware maker Paragon Solutions.

eSecurity Planet
FEBRUARY 17, 2025
It warns you about phishing attempts. McAfees most basic plan consists of a VPN and text scam detection features that Microsoft Defender lacks. It tries to provide features like anti-ransomware, anti-spyware, and parental controls, but that still keeps it behind. McAfee also doesnt offer spyware detection, but Defender does.

Webroot
OCTOBER 25, 2021
Even strong security can’t prevent an account from being hacked if account credentials are stolen in a phishing attack, one of the most common causes of identity theft. In 2020, phishing scams spiked by 510 percent between January and February alone. Web-borne malware remains widespread.

Security Affairs
MARCH 8, 2020
The emails provide updates on the Coronavirus outbreak, it includes stats on the epidemic and contains an email of corona-virus@caramail.com that is likely used for phishing purposes. See Using Caution with Email Attachments and Avoiding Social Engineering and Phishing Scams for more information.

Security Affairs
MAY 8, 2020
Group-IB, a Singapore-based cybersecurity company, observed the growth of the lifespan of phishing attacks in the second half of 2019. Figure 1 The distribution of web-phishing among target categories . CERT-GIB’s findings indicate that phishing attack perpetrators have revised their so-called target pool. Target reshuffle.

Security Boulevard
MARCH 17, 2025
Malware North Korean government hackers snuck spyware on Android app store TechCrunch APT threat actors associated with the North Korean government uploaded spyware "KoSpy" to Google Play. According to Lookout, these nation-state threat actors also tricked some users into downloading KoSpy in likely targeted attacks.

Hot for Security
JUNE 15, 2021
Given the portability and myriad of functionalities, mobile devices are highly susceptible to cyber threats, including malware, spyware and phishing attempts that may compromise that precious piece of tech we keep in our pocket and any information stored on it. Avoid smishing and phishing attacks.

Malwarebytes
OCTOBER 26, 2021
Some people get so convinced they have spyware on their system that they contact our support team to help them get rid of it. Social media and scams. There are many kinds of Bitcoin scams to be found on YouTube, Twitter, and other platforms. More Facebook concerns. Every Facebook user will have seen posts like this.

eSecurity Planet
JUNE 16, 2022
Cisco Umbrella , analyzing the threat environment for 2022, found that 86% of organizations experienced phishing, 69% experienced unsolicited crypto mining, 50% were affected by ransomware, and 48% experienced some form of information-stealing malware. Phishing attacks continue to dominate cyber threats. Crimeware and spyware.

Hot for Security
JUNE 14, 2021
Most security threats faced by regular users arrive via the Internet, whether it’s a malicious app or a rigged website , a scam delivered through the user’s social media channels, or a phishing scheme carried out via email or SMS. A well-timed phishing attack is all it takes to steal a user’s personal or financial information.

Security Affairs
SEPTEMBER 1, 2024
CISA adds Versa Director bug to its Known Exploited Vulnerabilities catalog International Press – Newsletter Cybercrime Telegram messaging app CEO Durov arrested in France Thousands of travelers, airport operations impacted by Port of Seattle cyberattack Hacker who stole 3 billion US data was discovered and is Brazilian Pressure Grows in Congress to (..)

Security Affairs
APRIL 24, 2022
If you want to also receive for free the newsletter with the international press subscribe here. T-Mobile confirms Lapsus$ had access its systems Are you using Java 15/16/17 or 18 in production? Patch them now!

Security Affairs
NOVEMBER 11, 2023
Police seized BulletProftLink phishing-as-a-service (PhaaS) platform Serbian pleads guilty to running ‘Monopoly’ dark web drug market McLaren Health Care revealed that a data breach impacted 2.2 Virtual Kidnapping: AI Tools Are Enabling IRL Extortion Scams How a ‘Refund Fraud’ Gang Stole $700,000 From Amazon Info from 5.6

Identity IQ
FEBRUARY 18, 2021
A common example is phishing. Phishing is a type of social engineering attack whereby hackers send fictitious emails or other communication , from what appears to be a trusted company, to induce victims to reveal personal information such as passwords, usernames or payment details. Awareness of Phishing Scams.

BH Consulting
OCTOBER 6, 2022
Is it just us, or is phishing everywhere right now? Banks and insurance companies are telling customers to be wary of scam messages. Social engineering techniques, such as phishing, target not the systems but the people using them. Social engineering techniques, such as phishing, target not the systems but the people using them.

Security Boulevard
FEBRUARY 17, 2025
Google's reCAPTCHA is not only useless, it's also basically spyware Techspot This study demonstrates Google's reCAPTCHA v2 and v3 are flawed and don't actually keep out bots.

Identity IQ
FEBRUARY 21, 2023
The trojan horse can be hidden in software or attachments that, if downloaded, install different spyware and viruses on your device. This spyware and viruses can cause many problems on your device and compromise personal details. Phishing Phishing is a very costly threat to individuals. This is a trap.

Malwarebytes
MAY 10, 2023
Just check out the following stats from last year: 18 percent of clicked phishing emails in 2022 came from a mobile device. Or even scarier—a backdoor could be placed or a nefarious piece of spyware. ” The number of phishing sites targeting mobile has shot up by 50 percent from 2019 to 2021. . And the kicker?
Malwarebytes
JUNE 5, 2024
Don’t forget to also use Browser Guard on your desktop to block ad trackers and scam sites from your browser. You shouldn’t have to guess whether the next attack will compromise your Wi-Fi connection, browser, or files through phishing emails, spyware, or malware. Let the technology do this for you.

Security Boulevard
MAY 3, 2021
Millions in the UK Targeted by Malware via a DHL Scam Text Message. Millions of UK citizens received a scam text message (aka smashing) which impersonated DHL in April. NCSC advice FluBot: Guidance for ‘package delivery’ text message scam . Flubot: Warning over SMS “Package Delivery” Scam Message which Delivers Android Malware.

IT Security Guru
FEBRUARY 13, 2023
With so many well known banking sites falling short when it comes to blocking fraudsters, cybersecurity experts at VPNOverview have compiled a list of 12 safety tips to keep your money safe from malware and phishing scams. What are the possible dangers of online banking?

Malwarebytes
AUGUST 25, 2022
In the first half of the year, we observed spiking detections of threats associated with tech support scams. These threats install applications on the system that create fake error messages, urging the user to call a "help center" that is, in reality, a scam operation. United States manufacturing family threat detections pie chart.

Identity IQ
MAY 7, 2021
Once they have access to an account with sufficient authority, cybercriminals can use that trusted email address to scam other companies into making fraudulent payments or just distribute malware en mass. Research by Verizon has shown that a third of all breaches in the past year involved phishing scams.

eSecurity Planet
SEPTEMBER 29, 2021
Integrated one-on-one Spyware HelpDesk support. They provide a first line of defense against fake, scam, phishing and spoofed websites, created to harm devices, compromise security, and even steal personal information. Anti-phishing, spam and fraud prevention. Rapid malware scan for quick and easy detection of threats.

Malwarebytes
SEPTEMBER 27, 2021
Uber scam lures victims with alert from a real Uber number Teaching cybersecurity skills to special needs children with Alana Robinson: Lock and Code S02E18. Other cybersecurity news.

SiteLock
AUGUST 27, 2021
You may be most familiar with computer malware such as Trojan viruses and spyware, which can be used to retrieve sensitive data from a computer or even take control of the system. Phishing attacks may be commonly associated with email scams, but they can be executed through websites as well.

Security Boulevard
FEBRUARY 10, 2025
Spyware maker Paragon terminates contract with Italian government: media reports TechCrunch This campaign was included in Week 5 of the Privacy Roundup , where Meta disrupted a campaign on WhatsApp targeting approximately 100 users with Paragon Spyware. this is certainly a news item worth paying attention to.

Security Boulevard
JANUARY 25, 2022
Exposing a Currently Active Domain Portfolio of Tech Support Scam Domains – An OSINT Analysis. Exposing a Currently Active NSO Spyware Group’s Domain Portfolio – WhoisXML API Analysis. Exposing a Currently Active Rock Phish Domain Portfolio – Historical OSINT.

SecureWorld News
APRIL 11, 2023
According to an FBI "Scams and Safety" brief , which also discusses system and data protection and protecting money information: Be careful when connecting to a public Wi-Fi network and do not conduct any sensitive transactions, including purchases, when on a public network.

Security Boulevard
AUGUST 1, 2024
Cyber threats such as phishing, identity theft, and malware attacks are ever-present dangers that can compromise our privacy and security. Cyber threats such as phishing, identity theft, and malware attacks are ever-present dangers that can compromise our privacy and security. Scrub the Cyber Grime Good cyber hygiene is key.

SecureList
NOVEMBER 22, 2022
Despite these uncovered campaigns, attackers were still more likely to hunt for cryptocurrency using phishing, offering dubious cryptocurrency exchange platforms, and launching cryptojacking to illicitly mint cryptocurrency. According to the freshest data on DeFi, every hour 15 newly deployed scams against smart contracts are detected.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content