CrowdStrike 2024 Global Threat Report: 6 Key Takeaways
Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.

Tech Republic Security
FEBRUARY 26, 2024
Identity-based and social engineering attacks still take center stage, according to the CrowdStrike 2024 Global Threat Report.

Security Boulevard
MAY 4, 2023
The first quarter of 2023 saw a notable rise in cyberattacks targeting trust in established tech brands Microsoft and Adobe, according to the Avast Q1 2023 Threat Report. The report also revealed a 40% increase in the share of phishing and smishing attacks from the previous year.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Security Boulevard
APRIL 14, 2023
Cryptocurrency-related phishing attacks are on the rise, with a report from Kaspersky recording an increase of 40% in 2022 compared to the previous year. The post Cryptocurrency Phishing Threats Luring New Victims appeared first on Security Boulevard.

SecureWorld News
JUNE 29, 2023
Cybersecurity firm Zimperium recently released its 2023 Global Mobile Threat Report 2023 , revealing a concerning increase in sophisticated attacks targeting mobile devices. The report sheds light on the escalating threat landscape faced by mobile-powered businesses.
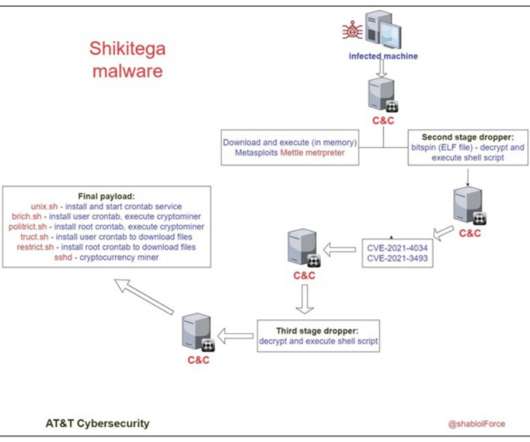
eSecurity Planet
SEPTEMBER 15, 2022
Employees should be trained against various social engineering and phishing attacks, as it’s a classic vector used by cybercriminals to deploy malware. AT&T labs provided a list of IoCs (indicators of compromise) that system administrators can use to add specific rules to security solutions.

Webroot
FEBRUARY 11, 2021
As we mentioned in a previous blog , hackers come in many forms, but their methods can generally be classified into three distinct types of cybercriminals: The Impersonator – Hackers that pretend to be others, often using social engineering and human psychology to trick users. government stimulus payments are also on the rise.

BH Consulting
SEPTEMBER 14, 2023
Its 2023 phishing threats report combines findings from email security data with a survey of security decision makers. MORE As social engineering tactics improve, how can potential victims fight back? The World Economic Forum has a useful blog with tips on safeguarding against BEC scams.
Let's personalize your content