Cybersecurity Insights with Contrast CISO David Lindner | 1/26/24
Security Boulevard
JANUARY 26, 2024
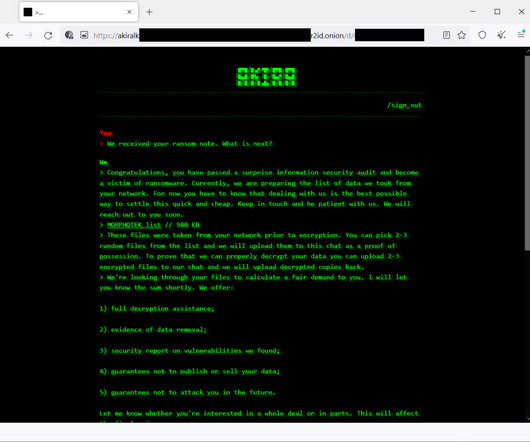
The attackers reportedly got in through an old testing environment, which seemingly had no multi-factor authentication (MFA) stopping them. Lesson learned: Just because it’s not a production system doesn't mean it can't be used as an avenue to get into your production systems. Threat models? It all matters.













































Let's personalize your content