Best Ransomware Protection
Hacker Combat
APRIL 6, 2022
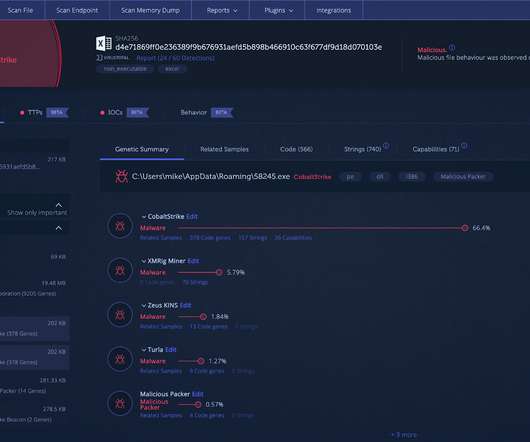
Ransomware attacks targeting governments, businesses, hospitals, and private individuals are rising. You are neither safe on your private nor public network, as ransomware can encrypt your files and hold them hostage. We will look at the features of some of the best ransomware protection that you can run on your systems.


















































Let's personalize your content