Ransomware: A Beginner’s Guide to Threat Detection
Tech Republic Security
JUNE 7, 2022
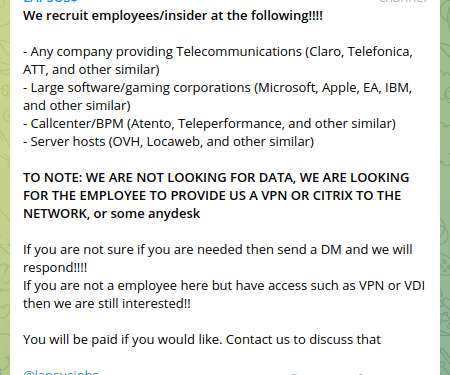
If you have been following the news, you’ll have most certainly been bombarded by the term ransomware. Due to the increased awareness of ransomware, one may think that this is a new phenomenon. The post Ransomware: A Beginner’s Guide to Threat Detection appeared first on TechRepublic. But it’s not.
















































Let's personalize your content