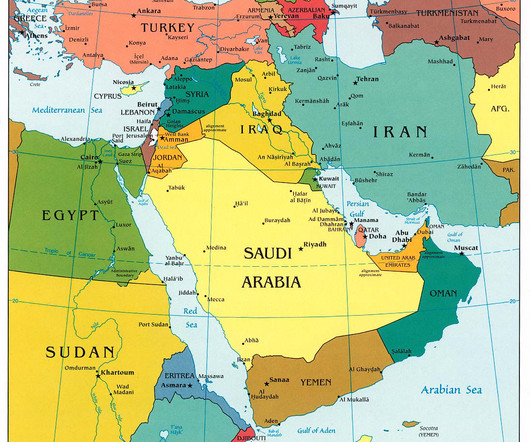
DuneQuixote campaign targets the Middle East with a complex backdoor
Security Affairs
APRIL 21, 2024
The malware is developed in C/C++ without utilizing the Standard Template Library (STL), and certain segments are coded in pure Assembler.” Additionally, it incorporates anti-analysis measures and checks to prevent connections to C2 resources. ” reads the analysis published by Kaspersky. ” concludes the report.






































Let's personalize your content