Facebook Meta uncovers Social Media Espionage
CyberSecurity Insiders
MAY 4, 2023
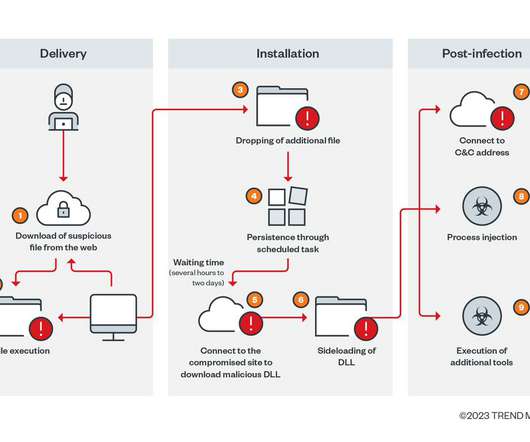
According to the security teams’ analysis, three different threat actors were involved in this campaign and were assigned to focus their malicious goals on users from South Asian countries such as India, Bangladesh, Pakistan, Maldives, Sri Lanka, Nepal, Bhutan, Afghanistan, and others.

















































Let's personalize your content