Cybercriminals leaked massive volumes of stolen PII data from Thailand in Dark Web
Security Affairs
JANUARY 22, 2024
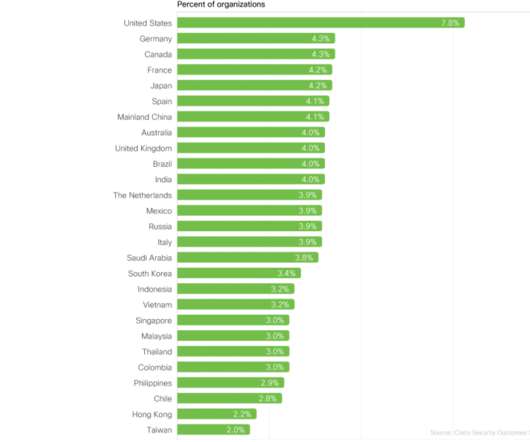
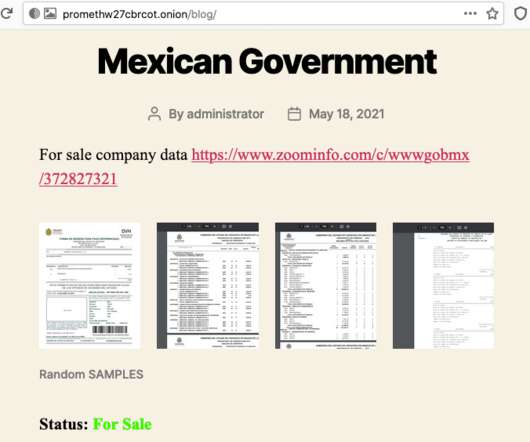
Resecurity researchers warn of massive leak of stolen Thai personally identifiable information (PII) on the dark web by cybercriminals. There are reports of cybercriminals, one known in the shadowy corners of the Dark Web as Naraka, circulating large amounts of stolen personal identifiable information (PII) of Thai citizens.
















































Let's personalize your content