GUEST ESSAY: Adopting an ‘assume-breach mindset’ to defend company networks in 2024
The Last Watchdog
DECEMBER 10, 2023
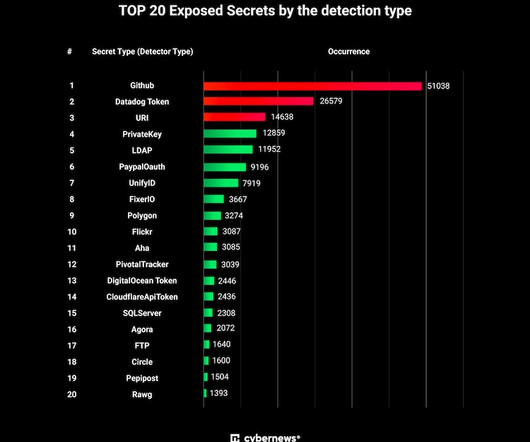
It forces IT professionals to take a realistic view of their security posture and adapt to the evolving threat landscape. Embracing this approach is resource-intensive and may introduce complexities. Here are some drawbacks of this mindset: •Resource intensive. Available resources. Realistic perspective.

















































Let's personalize your content