Attack Surface Management for the Adoption of SaaS
CyberSecurity Insiders
SEPTEMBER 20, 2022
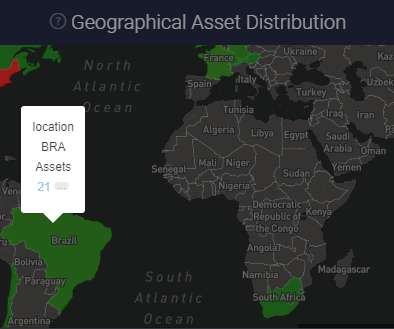
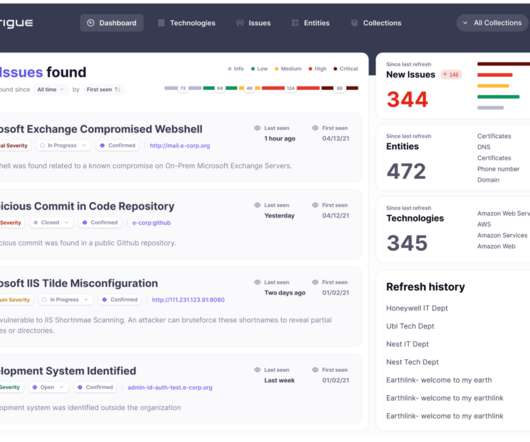
By Alfredo Hickman, head of information security, Obsidian Security. While much of the conversation centered around managing the attack surface around on-premise environments and cloud infrastructure, it was interesting to me that not much was said about SaaS. However, SaaS attack surface management is not impossible.















































Let's personalize your content