RSAC Fireside Chat: APIs are wondrous connectors — and the wellspring of multiplying exposures
The Last Watchdog
MAY 1, 2024
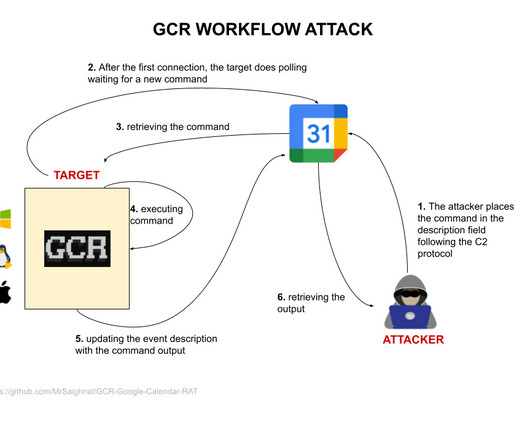
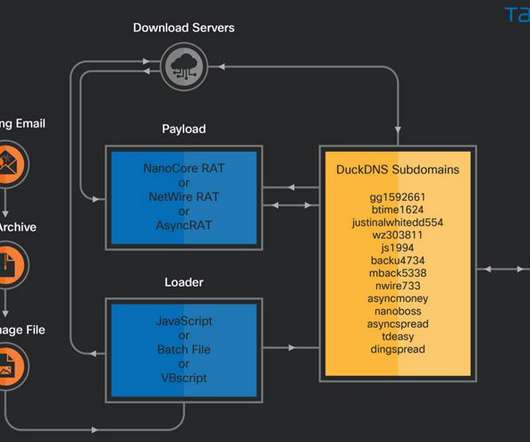
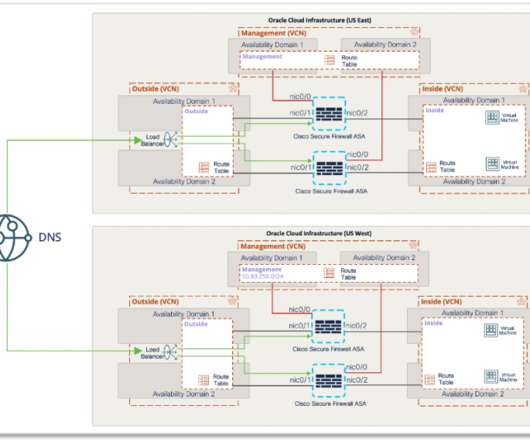
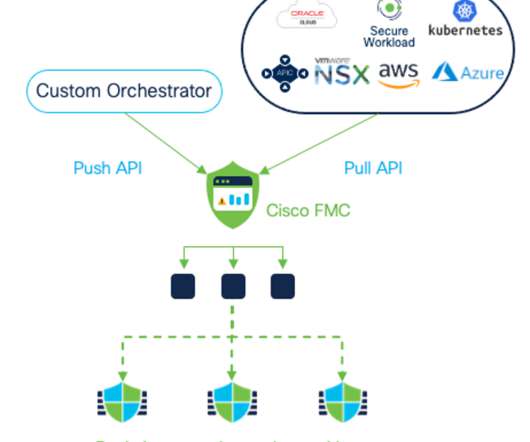
We discussed how enterprises in 2019 were deep into making the transition from on-premises networks to cloud-centric, edge-oriented operations when the global pandemic hit. Instantly, API connections skyrocketed to support connected services for a quarantined world. Securing them has become paramount.













































Let's personalize your content