News alert: ThreatHunter.ai stops hundreds of ransomware attacks, nation-state threats in 48 hours
The Last Watchdog
FEBRUARY 27, 2024
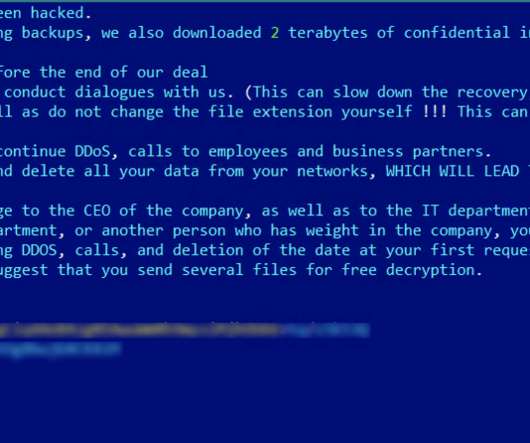
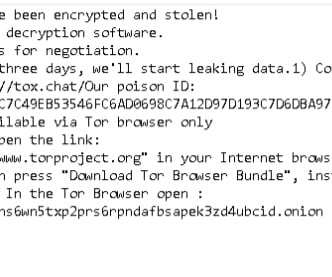
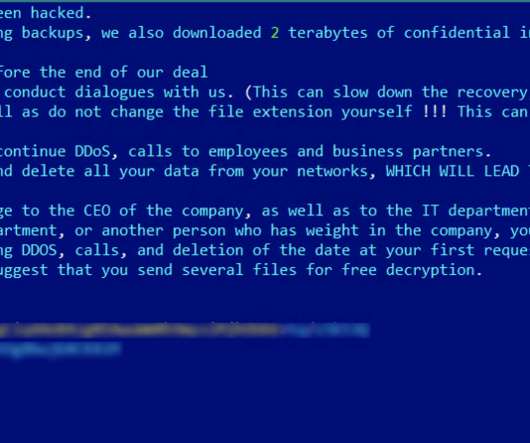
27, 2024 — The current large surge in cyber threats has left many organizations grappling for security so ThreatHunter.ai Drawing on recent events and the resilient nature of cyber threats, as highlighted in an insightful piece on the LockBit ransomware saga, it’s evident that the cybersecurity landscape is more volatile than ever.













































Let's personalize your content