Top CVE Trends — And What You Can Do About Them
The State of Security
JUNE 1, 2022
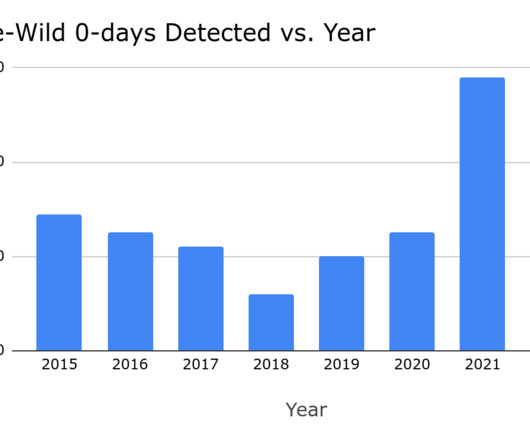
In addition to implementing the right tools and resources, and hiring skilled professionals with the right cybersecurity education and experience, organizations should be aware of the latest CVEs. What Is a CVE? The post Top CVE Trends — And What You Can Do About Them appeared first on The State of Security.




















Let's personalize your content