GUEST ESSAY: The role ‘deep learning’ AI can play relieving security teams of debilitating stress
The Last Watchdog
JANUARY 29, 2023
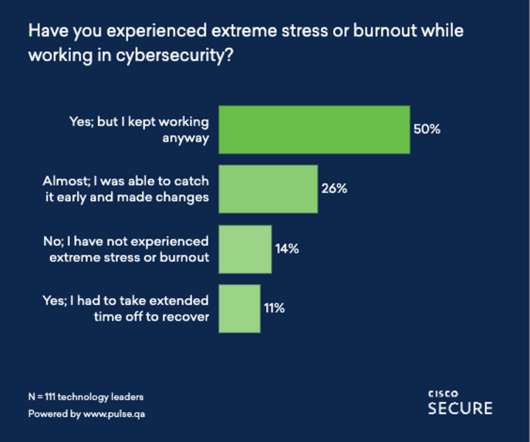
The cybersecurity profession can be very rewarding, but at the same time quite taxing. Related: Equipping SOCs for the long haul In fact, stress factors have risen to where some 45 percent of the security professionals polled in Deep Instinct’s third annual Voice of SecOps report said they’ve considered leaving the industry altogether.














































Let's personalize your content