Burger King forgets to put a password on their systems, again
Security Affairs
AUGUST 2, 2023
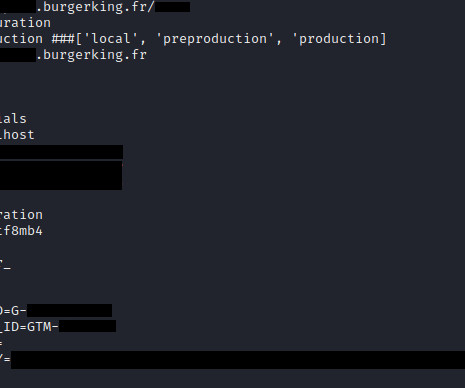
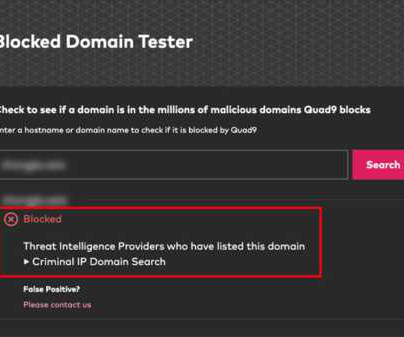
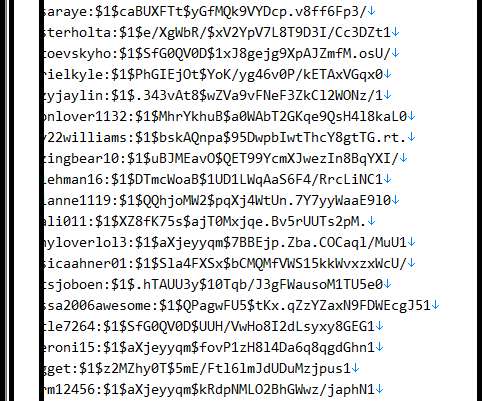
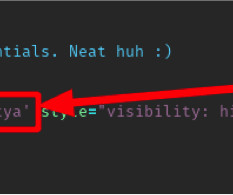
Among other sensitive data, the file contained credentials for a database. While, due to legal reasons, the researchers could not check what exactly was stored in the database, there were likely job posts and perhaps other data entered by the applicants. Then they’d be able to execute arbitrary JavaScript code on the website.










































Let's personalize your content