Detecting Cobalt Strike and Hancitor traffic in PCAP
Security Boulevard
MAY 31, 2021
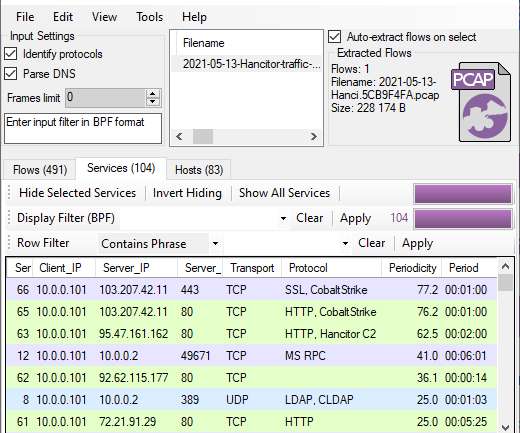
Your browser does not support the video tag. OMG he's analyzing Windows malware on a Windows PC!!! This video shows how Cobalt Strike and Hancitor C2 traffic can be detected using CapLoader. I bet you're going: ?? Relax, I know what I'm doing. I have also taken the precaution of analyzing the PCAP f[.].

























Let's personalize your content