Threat Model Thursday: 5G Infrastructure
Adam Shostack
JULY 1, 2021
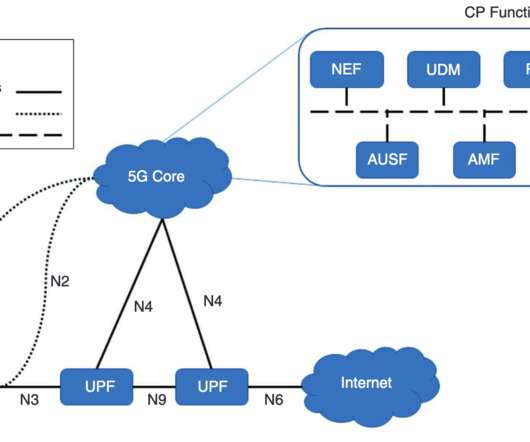
The US Government’s lead cybersecurity agencies (CISA, NSA, and ODNI) have released an interesting report, Potential Threat Vectors To 5G Infrastructure. Press release ), and I wanted to use this for a Threat Model Thursday, where we take a respectful look at threat modeling work products to see what we can learn.

















































Let's personalize your content