What is Dynamic Application Security Testing (DAST)?
eSecurity Planet
JUNE 22, 2023
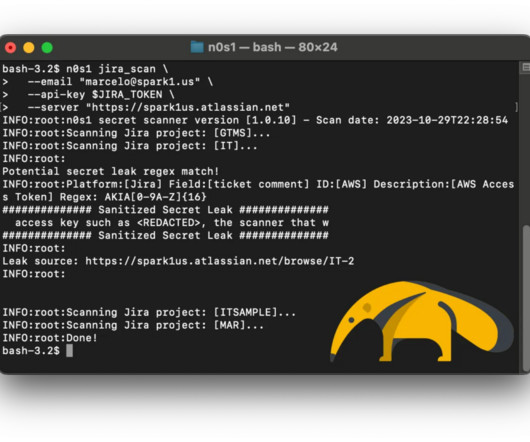
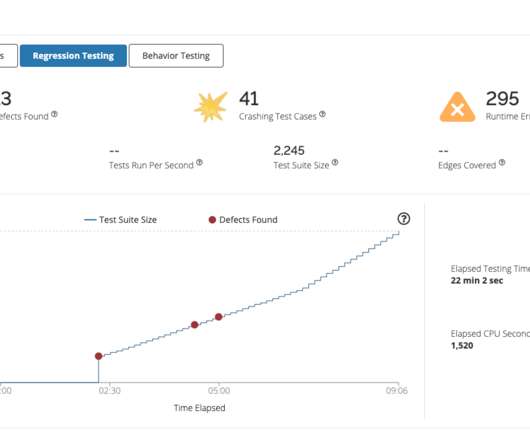
Dynamic Application Security Testing (DAST) combines elements of pentesting, vulnerability scanning and code security to evaluate the security of web applications. By doing this, DAST helps determine how secure the web application is and pinpoint areas that need improvement. Why is DAST Important for Application Security?












































Let's personalize your content