6 Ways To Secure Your Home Construction Site
SecureBlitz
APRIL 12, 2022
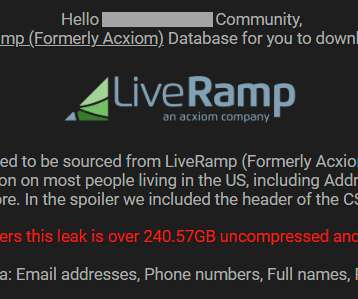
This post will show you how to secure your home construction site. According to the reports, job site theft is a widespread and rising problem that costs the construction sector more than $1 billion each year. However, there.





























Let's personalize your content