CVE-2021-31166 Windows HTTP flaw also impacts WinRM servers
Security Affairs
MAY 23, 2021
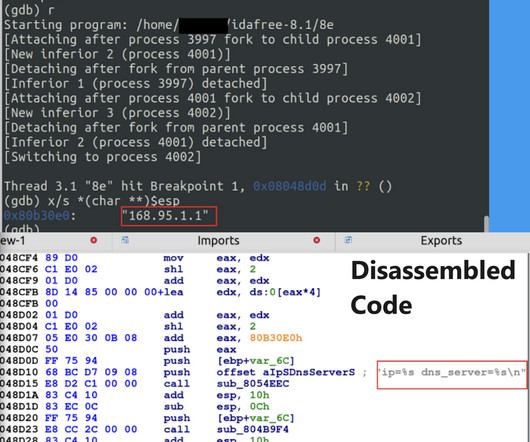
The flaw is wormable and affects different versions of Windows 10, Windows Server 2004 and Windows Server 20H2. The security researcher Axel Souchet has published over the weekend a proof-of-concept exploit code for the wormable flaw that impacted Windows IIS. I finally found time to answer my own question. WinRM *IS* vulnerable.







































Let's personalize your content