2020 sees huge increase in records exposed in data breaches
Tech Republic Security
JANUARY 21, 2021
The number of breaches may have fallen, but the number of exposed records hit a high not seen since 2005, says Risk Based Security.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Tech Republic Security
JANUARY 21, 2021
The number of breaches may have fallen, but the number of exposed records hit a high not seen since 2005, says Risk Based Security.

The Last Watchdog
APRIL 24, 2019
Accounting for third-party risks is now mandated by regulations — with teeth. Allen is a widely respected thought leader on this topic, having launched Shared Assessments in 2005 as an intel-sharing and training consortium focused on third-party risks. That out of the way, business can proceed with less risk.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

The Last Watchdog
JANUARY 30, 2019
Related: Atrium Health breach highlights third-party risks. Third-party cyber risks are likely to persist at the current scale for a while longer. According to a recent Ponemon Institute study , some 59% of companies experienced a third-party data breach in 2018, yet only 16% believe they are effectively mitigating third-party risk.

SecureBlitz
OCTOBER 1, 2022
In this interview, we spoke with David Monnier, Chief Evangelist at Team Cymru, a risk management solution launched in 2005 with a network that extends to 143 CSIRT teams in 86 countries and over 1,000 network operators and ISP community that helps keep the internet safe. Team Cymru has released the findings from their State […].

SecureWorld News
AUGUST 18, 2022
Very few new computers have hard disk drives, or drives that rotate at the speed of 5400 rpm, so the risk for new devices is essentially nonexistent. Do you have a laptop from 2005 still laying around? Yet, t he MITRE Corporation still made the decision to list it on the register of Common Vulnerabilities and Exposures (CVEs).

Security Affairs
MAY 2, 2019
The availability of 10KBLAZE PoC exploits for old SAP configuration issue poses a severe risk of attacks for business applications. The risk of cyber attacks against SAP systems is increased after security researchers released PoC exploits for old SAP configuration flaws. ” reads the analysis published by Onapsis.

Malwarebytes
SEPTEMBER 22, 2022
In Firefox 105 a total of seven vulnerabilities were patched, three of which received the security risk rating "high". One with the rating “high” risk. Since UTF-8 as character encoding was introduced in 2005, there may be still some URLs which use a different encoding.

Centraleyes
MARCH 3, 2025
Similarly, the states Information Security Breach and Notification Act (2005) was one of the earliest breach notification laws in the U.S., The SHIELD Act: Strengthening New Yorks Data Security The SHIELD Act , passed in 2019, builds on New Yorks earlier Information Security Breach and Notification Act (2005).

Security Affairs
MARCH 27, 2022
According to Binding Operational Directive (BOD) 22-01: Reducing the Significant Risk of Known Exploited Vulnerabilities , FCEB agencies have to address the identified vulnerabilities by the due date to protect their networks against attacks exploiting the flaws in the catalog.
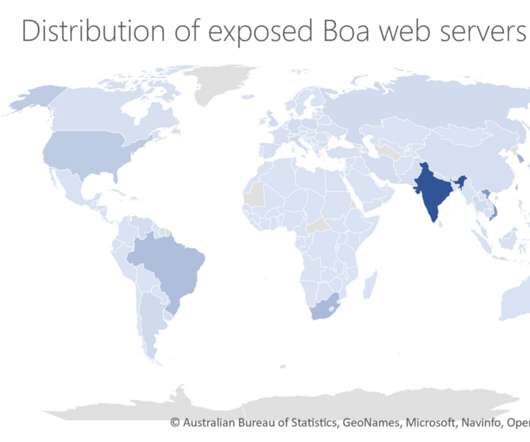
Security Affairs
NOVEMBER 24, 2022
The experts pointed out that Boa has been discontinued since 2005. ” Microsoft experts explained that despite Boa being discontinued in 2005, many vendors across a variety of IoT devices and popular software development kits (SDKs) continue to use it. ” reads the report published by Microsoft. ” concludes the report.

The Last Watchdog
MAY 3, 2021
All of the technical innovation cybersecurity vendors are churning out to deal with ever-expanding cyber risks, at the end of the day, come down to protecting encrypted data. And since 2005 or so, one area of focus has been on sharpening the math formulas that make attribute-based encryption possible.

Malwarebytes
JANUARY 12, 2024
is an open-source CMS that’s been around since 2005, and has been one of the most popular CMS platforms by market share for much of that time. Cybersecurity risks should never spread beyond a headline. Many companies, from small outfits to large enterprises, use a CMS in some form to manage their websites.

Malwarebytes
FEBRUARY 6, 2023
In 2005, one malware install which needed the.NET framework to run would helpfully install the whole thing for you if you didn’t have it. For one final slice of additional context, 2005 was also a key year for security happenings. By curious coincidence, the ASC also came into existence in 2005. Stay safe out there!

The Last Watchdog
JUNE 23, 2021
The challenge of embracing digital transformation while also quelling the accompanying cyber risks has never been greater for small- and mid-sized businesses. Somehow SMBs must keep pace competitively, while also tamping down the rising risk of suffering a catastrophic network breach. Remote desktop risks.

The Last Watchdog
MARCH 29, 2022
They’re now the norm and security teams must assess and manage the risk of these stacks.”. Complex and evolving cyber risks need to be resolved, for instance, when it comes to securing human and machine identities, tightening supply chains, mitigating third-party risks, protecting critical infrastructure and preserving individuals’ privacy.

Security Affairs
SEPTEMBER 4, 2021
. “For example, the SEC brought a number of enforcement actions against individuals and companies who made false and misleading statements about alleged business opportunities in light of damage caused by Hurricane Katrina in 2005. Know that promises of fast and high profits, with little or no risk, are classic signs of fraud.

IT Security Guru
JUNE 28, 2022
As a result, it’s difficult to gauge how at risk an organisation is. A conservative estimate from 2002 predicted that by 2005, cyber insurance would boast a global market worth $2.5 Among security professionals, cyberattacks are no longer viewed as a risk, but as an inevitability. The story so far. It didn’t take off.

Malwarebytes
AUGUST 18, 2022
Mechanical drives have a whole lot of vibration going on inside, and this is where the drives become vulnerable to very peculiar forms of frequency based risk. As I close the lid on my 2005 Windows XP laptop for the last time, never a truer word was spoken.

Malwarebytes
FEBRUARY 23, 2024
is an open-source CMS that’s been around since 2005, and has been one of the most popular CMS platforms by market share for much of that time. Cybersecurity risks should never spread beyond a headline. posted details about four vulnerabilities it had fixed in its Content Management System (CMS), and one in the Joomla!
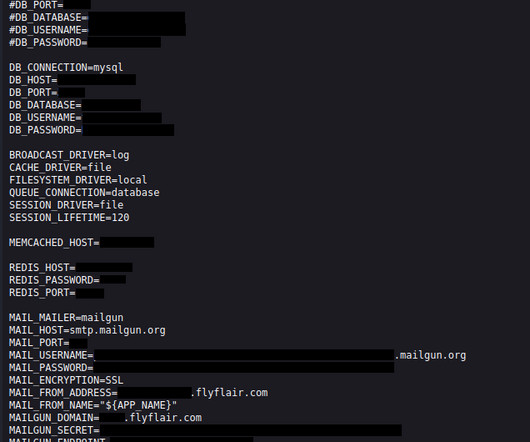
Security Affairs
SEPTEMBER 26, 2023
This increases the risk of passengers’ personal information, such as emails, names, or addresses, ending up in the wrong hands. Flyflair.com belongs to the Canadian ultra-low-cost carrier Flair Airlines, founded in 2005. The leak consisted of publicly accessible environment files hosted on the flyflair.com website.

The Last Watchdog
JANUARY 7, 2019
Initially introduced in 2005, CVSS is a framework for rating the severity of security vulnerabilities in software. The risks are growing for two reasons. Kfir: What we hope will happen is that the security monitoring systems will become more risk oriented, and more focused on reducing critical vulnerabilities. Barda: Yes.
Malwarebytes
OCTOBER 21, 2021
This time the update patches 19 vulnerabilities, of which 5 are classified as “high” risk vulnerabilities. Below are the CVEs attributed to external researchers that got rated as high risk: CVE-2021-37981 (High CVSS 7.7) : Heap buffer overflow in Skia.

Security Affairs
JUNE 13, 2023
According to the notice, threat actors had access to an older database of customers who had signed up for the Zacks Elite product between November 1999 through February 2005. The availability of the database in the cybercrime ecosystem poses a severe risk for the company users.

SC Magazine
FEBRUARY 18, 2021
First, the M1 chip represents a break from the Intel x86 architecture that Apple has relied on since 2005 – a move that came with promises of greater security. The new chip, which runs on reduced instruction set computing (RISC) technology, was developed by Advanced RISC Machines (ARM), which makes 32-bit and 64-bit versions.

Security Affairs
MAY 22, 2019
“We made an error when implementing this functionality back in 2005: The admin console stored a copy of the unhashed password. At the time Google did not reveal how many users might have been impacted, but we have to consider that currently, G Suite has 5 million enterprise customers potentially at risk. ” continues Google.

Adam Shostack
JANUARY 2, 2025
If youre not asking what can go wrong with each feature, and with the design as a whole, how will you attest that you have been following a risk-based approach for secure software development? Threat modeling is the activity that lets us identify those risks. Are your regulators going to move quickly or slowly?

The Last Watchdog
APRIL 1, 2020
Here are key takeaways: Storage efficiencies With so much data coursing through business networks, companies would be wise to take into consideration the value vs. risk proposition of each piece of data, Lahiri says. The value of data connected to a live project is obvious.

Security Affairs
JANUARY 23, 2020
The unprotected archive was containing support requests submitted to the tech giant from 2005 to December 2019. The availability of detailed logs in the hand of crooks could expose Microsoft customers to the risk of Tech support scams. . ” reads the post published by Microsoft.
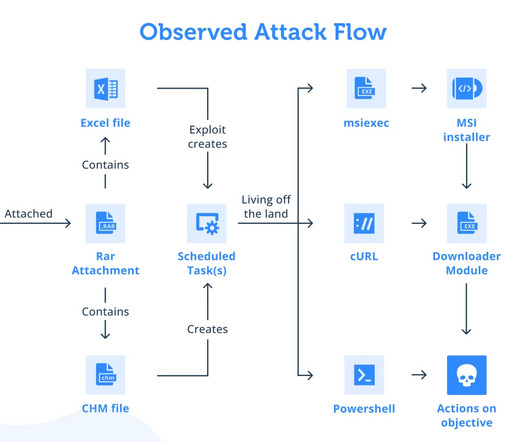
Security Affairs
MARCH 28, 2023
million records dating back to at least 2005 were also compromised in the data breach. “We are committed to working closely with impacted customers and applicants to minimise the risk and disruption to them, including reimbursing the cost if they choose to replace their ID document. 94% of these records (5.7

eSecurity Planet
MAY 20, 2021
billion in investments,” since 2005. Named the “Most Innovative Startup,” Apiiro was selected by a panel of esteemed judges for its Code Risk Platform. Apiiro Security Code risk platform 2019 Tel Aviv, Israel $35M. When considering the top 10, judges narrowed their deliberation to risk-focused Apiiro and identity-focused Strata.

Security Boulevard
APRIL 7, 2021
1 April 2005. Copyright (C) The Internet Society (2005). Young people are particularly at risk from the rising depravity in. RFC 4041 Routing Morality Section Requirements 1 April 2005. RFC 4041 Routing Morality Section Requirements 1 April 2005. RFC 4041 Routing Morality Section Requirements 1 April 2005.

Security Boulevard
JULY 21, 2022
Since 2005, SHA-1 has been regarded as unsafe against well-funded adversaries. For businesses still using the broken SHA-1, they were facing serious risks , including: Increased possibility of a collision or man-in-the-middle attack. What SHA-1 history can teach us? The presence of wildcard SSL certificates. Related Posts.

Doctor Chaos
APRIL 10, 2022
If you are more technically skilled and understand the security risks you might want to consider a Plex hosting server or a Seedbox. I’m about to order the small version of this as I’ve used the large size large since 2005. No more extortion fees to the hotel for watching a movie. Now you’re all set with this NoPay-Per-View option!

The Last Watchdog
MARCH 28, 2023
In the late 1990s (yes, that long ago), I created a youth training program called YouthLink that worked with at-risk youth in Washington, DC. Over my career, I have created three non-profits and two SaaS for profits, one of which I sold in 2005.

eSecurity Planet
APRIL 26, 2022
Company Sector Year Status Vicarius Vulnerability management 2022 Private Dragos ICS and OT security 2021 Private Safeguard Cyber Risk management 2021 Private CyberGRX Risk management 2019 Private Signifyd Fraud protection 2018 Private RedOwl Security analytics 2015 Acquired: Forcepoint. AllegisCyber Capital. AllegisCyber Investments.

Security Affairs
APRIL 8, 2019
Group-IB collects and analyses large amounts of unique and proprietary information to deliver tailored, trusted and actionable intelligence to predict risks, while preventing and mitigating any targeted attacks. About Group-IB. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

eSecurity Planet
FEBRUARY 10, 2022
Gartner first coined the term SIEM in 2005 to combine the technologies of security event management (SEM) and security information management (SIM). If log files are generated from infected endpoints, there is a risk in establishing a corrupted device as a baseline and future alerts are jeopardized. What is a SIEM?

Herjavec Group
NOVEMBER 16, 2020
When this trend started back in 2005, people preferred to shop while they were at the office, using fast computers and high-speed connections. Trust me, their corporate and personal email inboxes will be flooded with special incentives and opportunities to put your business at risk. But why Cyber Monday and not Saturday?

CyberSecurity Insiders
MAY 26, 2021
Metz brings the experience of a combat commander who led over 120,000 coalition troops belonging to Multi-National Corps-Iraq, during OPERATION IRAQI FREEDOM (2004-2005) combined with almost 40 years of commissioned service in the US Army. About Intelligent Waves, LLC.
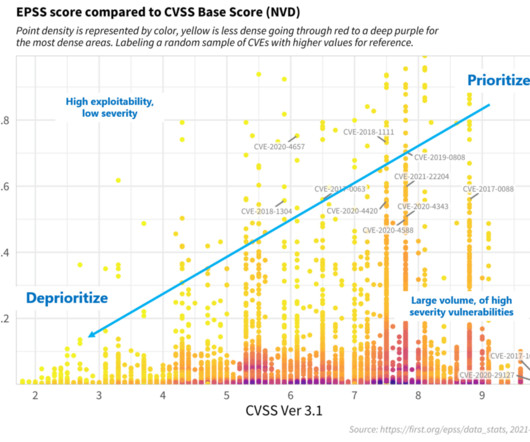
NopSec
OCTOBER 18, 2022
Accurately assessing the risk of software vulnerabilities is critical in order to prioritize remediation efforts given limited remediation resources. For vulnerabilities provided by the Common Vulnerability Enumeration (CVE) Program, many scanning systems utilize the Common Vulnerability Scoring System (CVSS) to assess risk.

Malwarebytes
OCTOBER 27, 2022
Even so, it seems more varied types of ad presentations were required to lower the risk of turning people away from streaming or watching altogether. Way back in 2005, dynamic ads were introduced to titles like The Matrix Online. A recent change to ad types and functionality made the ads “ less annoying ” overall.

Malwarebytes
JANUARY 16, 2024
As a member of the club, he competed in a local programming competition, helping the team to win in both 2005 and 2006. We don’t just report on threats—we remove them Cybersecurity risks should never spread beyond a headline. Despite this, he was active in extracurricular activities. In high school, he participated in a computer club.

eSecurity Planet
MARCH 21, 2025
Palo Alto Networks Best protection against network, endpoint, and remote asset attacks Headquarters: Santa Clara, California Founded: 2005 Annual Revenue: $7.52 Fortinet: Best for Network Security Perimeter Protection 15 $74.33 Bitdefender: Best for endpoint security and ransomware protection 3 No current available value 4.7

SiteLock
AUGUST 27, 2021
With the growing popularity of the Internet over the past decade, the retail holiday Cyber Monday debuted in 2005 as the online version of Black Friday. While this influx of holiday shoppers purchasing gifts for themselves and loved ones is great for online businesses, there are risks that come along with the rewards. 25% of U.S.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content