Oops: DanaBot Malware Devs Infected Their Own PCs
Krebs on Security
MAY 22, 2025
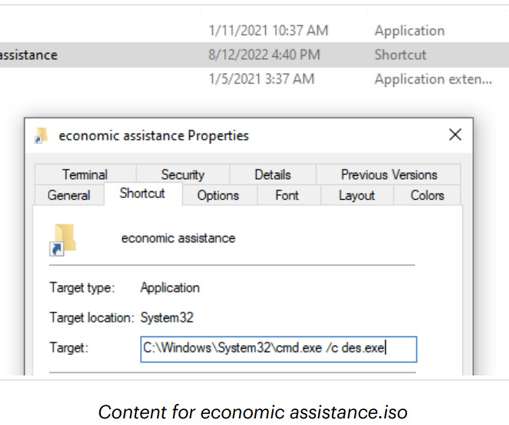
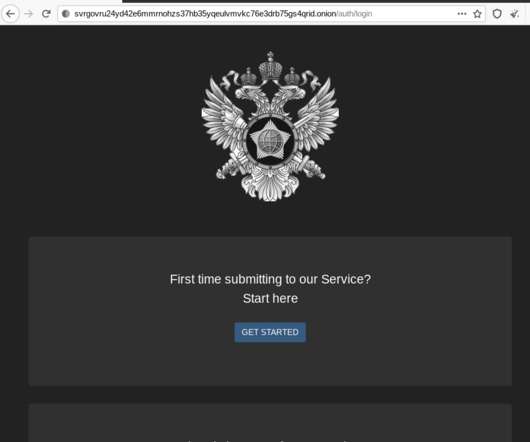
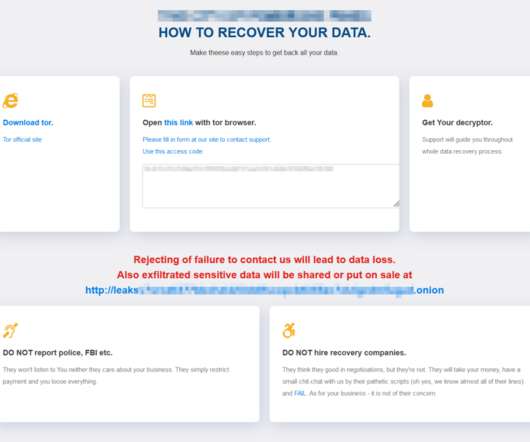
government today unsealed criminal charges against 16 individuals accused of operating and selling DanaBot , a prolific strain of information-stealing malware that has been sold on Russian cybercrime forums since 2018. DanaBot’s features, as promoted on its support site. DanaBot’s features, as promoted on its support site.





























Let's personalize your content