Qakbot is back and targets the Hospitality industry
Security Affairs
DECEMBER 18, 2023
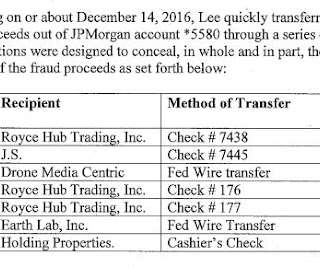
Experts warn of a new phishing campaign distributing the QakBot malware, months after law enforcement dismantled its infrastructure. Qakbot , also known as QBot, QuackBot and Pinkslipbot, is an info-stealing malware that has been active since 2008. Duck Hunt is one of the largest U.S.-led ” concludes Microsoft.









































Let's personalize your content