Who’s Behind the ‘Web Listings’ Mail Scam?
Krebs on Security
MARCH 23, 2020
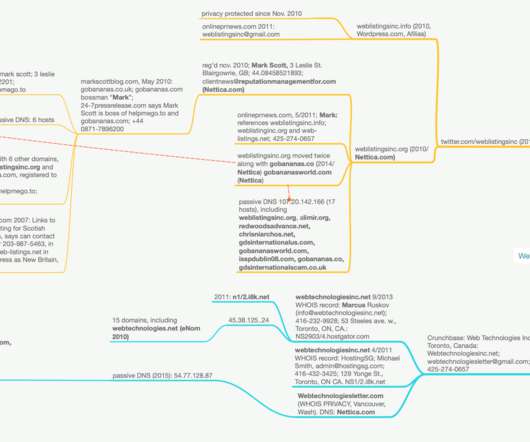
The story concluded that this dubious service had been scamming people and companies for more than a decade, and promised a Part II to explore who was behind Web Listings. A Twitter account for Web Listings Inc. Cached versions of this site from 2011 show it naming Web Listings Inc. Image: Better Business Bureau.






















Let's personalize your content