Mirai V3G4 botnet exploits 13 flaws to target IoT devices
Security Affairs
FEBRUARY 16, 2023
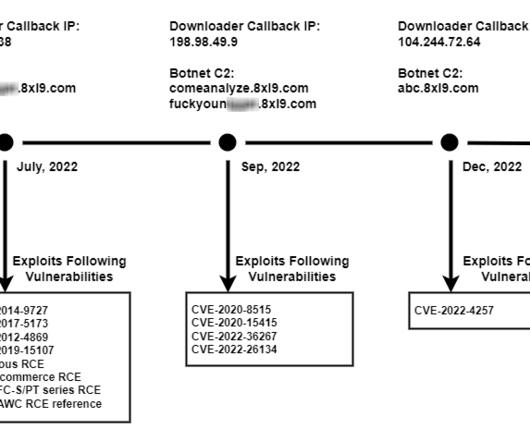
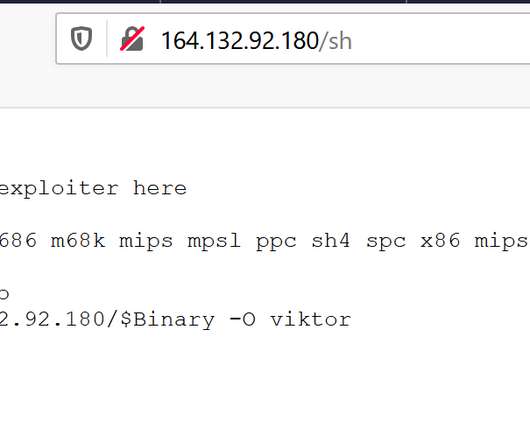
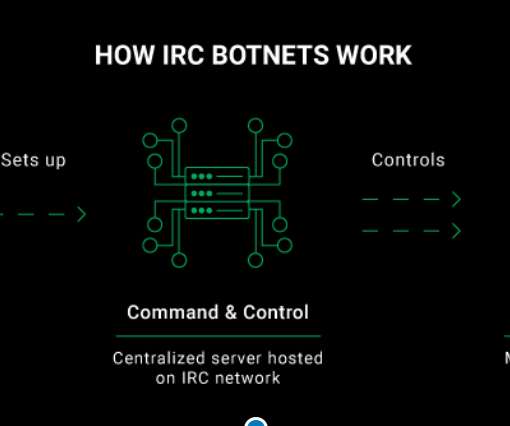
During the second half of 2022, a variant of the Mirai bot, tracked as V3G4, targeted IoT devices by exploiting tens of flaws. Palo Alto Networks Unit 42 researchers reported that a Mirai variant called V3G4 was attempting to exploit several flaws to infect IoT devices from July to December 2022.






























Let's personalize your content