Telegram offers fix to its non encrypted chat vulnerability
CyberSecurity Insiders
JULY 20, 2021
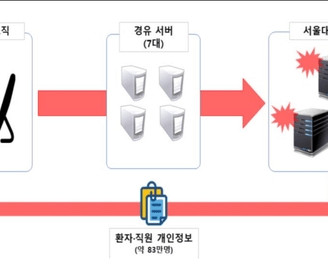
Telegram made it official that it has offered a security fix to non-encrypted chats that were previously vulnerable to cyber attacks through manipulated bots. Although all messages are encrypted on Telegram, the MTProto encryption is not available by default, as users need to opt-in for the end-to-end encryption.
































Let's personalize your content