French Firms Rocked by Kasbah Hacker?
Krebs on Security
MARCH 2, 2020
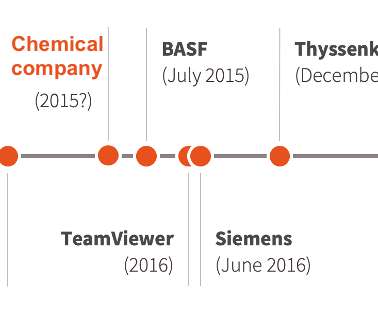
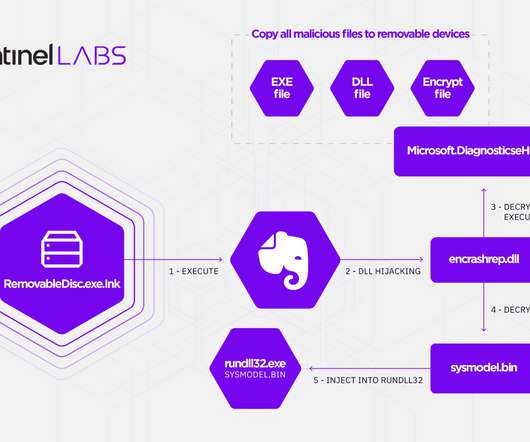
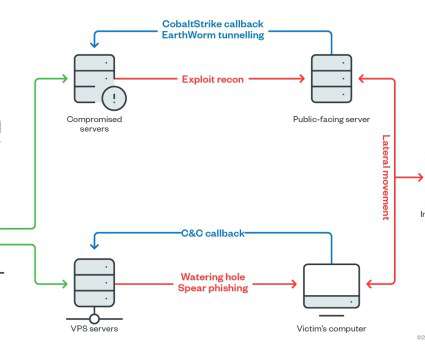
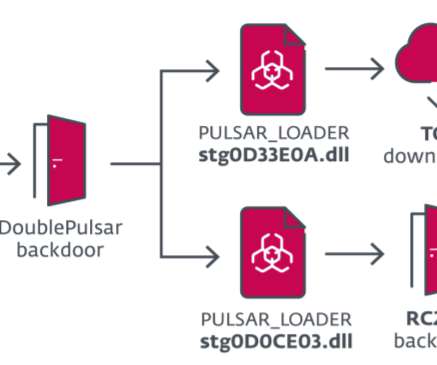
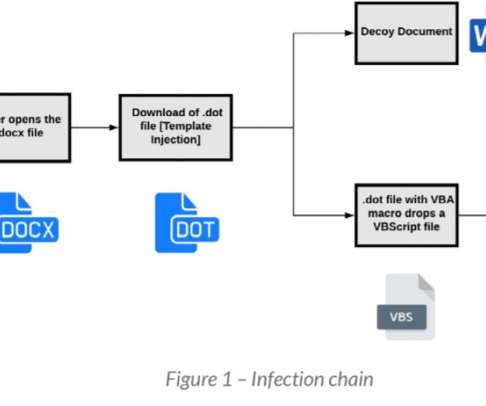
A large number of French critical infrastructure firms were hacked as part of an extended malware campaign that appears to have been orchestrated by at least one attacker based in Morocco, KrebsOnSecurity has learned.


























Let's personalize your content