What is the MITRE ATT&CK Framework?
Doctor Chaos
FEBRUARY 21, 2022
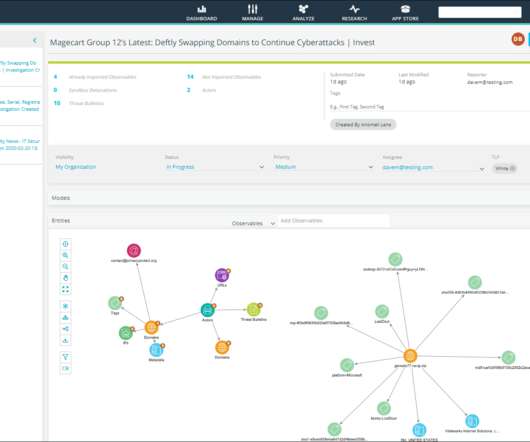
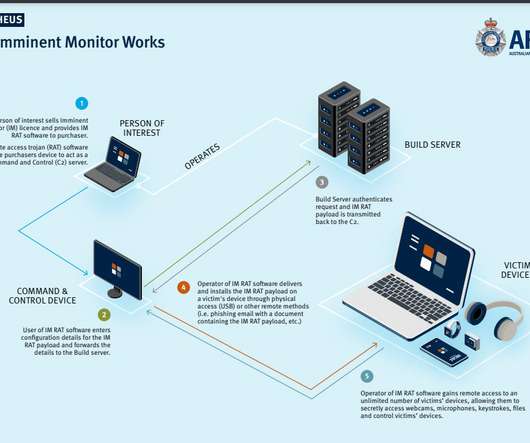
Created in 2013, the framework documents in detail countless cyberattack strategies. For example, by using the framework to learn about phishing attack strategies, you could develop a detailed training program for your team. Phishing attacks and ransomware attacks surged the most.























Let's personalize your content