Experian, You Have Some Explaining to Do
Krebs on Security
JULY 10, 2022
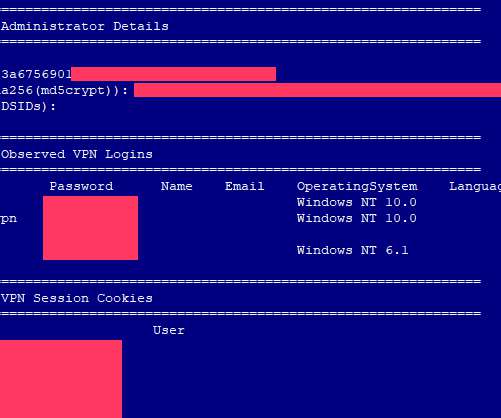
In both cases the readers used password managers to select strong, unique passwords for their Experian accounts. Turner said he created the account at Experian in 2020 to place a security freeze on his credit file, and that he used a password manager to select and store a strong, unique password for his Experian account.

































Let's personalize your content