DOGE as a National Cyberattack
Schneier on Security
FEBRUARY 13, 2025
Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks.
This site uses cookies to improve your experience. To help us insure we adhere to various privacy regulations, please select your country/region of residence. If you do not select a country, we will assume you are from the United States. Select your Cookie Settings or view our Privacy Policy and Terms of Use.
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.
Used for the proper function of the website
Used for monitoring website traffic and interactions
Cookies and similar technologies are used on this website for proper function of the website, for tracking performance analytics and for marketing purposes. We and some of our third-party providers may use cookie data for various purposes. Please review the cookie settings below and choose your preference.

Schneier on Security
FEBRUARY 13, 2025
Foreign adversaries typically spend years attempting to penetrate government systems such as these, using stealth to avoid being seen and carefully hiding any tells or tracks.

Krebs on Security
JULY 8, 2021
The attackers exploited a vulnerability in software from Kaseya , a Miami-based company whose products help system administrators manage large networks remotely. As its name suggests, CVE-2015-2862 was issued in July 2015. It’s from 2015!” “It’s a patch for their own software. .
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.

Schneier on Security
MARCH 4, 2021
Check Point has evidence that (probably government affiliated) Chinese hackers stole and cloned an NSA Windows hacking tool years before (probably government affiliated) Russian hackers stole and then published the same tool. This allows someone with a foothold on a machine to commandeer the whole box.

Security Affairs
JUNE 17, 2020
A CIA elite hacking unit that developed cyber-weapons failed in protecting its operations, states an internal report on the Vault 7 data leak. In March, Joshua Schulte , a former CIA software engineer that was accused of stealing the agency’s hacking tools and leaking them to WikiLeaks, was convicted of only minor charges.

Krebs on Security
NOVEMBER 13, 2019
In July 2016, KrebsOnSecurity published a story identifying a Toronto man as the author of the Orcus RAT , a software product that’s been marketed on underground forums and used in countless malware attacks since its creation in 2015. This week, Canadian authorities criminally charged him with orchestrating an international malware scheme.

Security Affairs
OCTOBER 12, 2018
Security agencies belonging to Five Eyes (United States, United Kingdom, Canada, Australia and New Zealand) have released a joint report that details some popular hacking tools. ” ~ Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Security Affairs – Five Eyes, hacking ).

Security Affairs
MAY 25, 2020
The issue could be exploited by supplying a malformed Java object to a specific listener on an vulnerable system. Administrators should update their Unified CCE installs as soon as possible. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – Unified CCE, hacking).

Security Affairs
SEPTEMBER 3, 2019
A baseboard management controller (BMC) is a specialized service processor that monitors the physical state of a computer, network server or other hardware device using sensors and communicating with the system administrator through an independent connection. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
APRIL 18, 2021
The Ukrainian national Fedir Hladyr (35), aka “das” or “AronaXus,” was sentenced to 10 years in prison for having served as a manager and systems administrator for the financially motivated group FIN7 , aka Carbanak. SecurityAffairs – hacking, FIN7). ” reads the press release published by DoJ. ” concludes DoJ.

Security Affairs
FEBRUARY 20, 2020
“The vulnerability is due to a system account that has a default and static password and is not under the control of the system administrator.” ” An attacker could exploit the flaw by using this default account to connect to a vulnerable system and obtain read and write access to system data.

Security Affairs
MARCH 1, 2019
“Mail server, domain administrator and system administrator accounts were all affected, giving cyberespions access to the past and current passwords of more than 2,000 ICAO system users. The agency thus becoming a one-stop shop for the hacking of all other players in the aerospace industry.”.

Security Affairs
JUNE 27, 2019
“The hacking campaign, known as “ Cloud Hopper ,” was the subject of a U.S. ” The report attributed the cyberespionage campaign to the China-linked APT10 (aka Menupass, and Stone Panda), the same group recently accused of hacking telco operators worldwide. SecurityAffairs – Cloud Hopper, hacking).

Security Affairs
OCTOBER 21, 2021
The two individuals, Aleksandr Skorodumov (33) of Lithuania, and Pavel Stassi (30) of Estonia, administrated the bulletproof hosting service between 2009 and 2015. Stassi conducted several administrative tasks for the group, such as registering webhosting and financial accounts using stolen and/or false personal information.

Security Affairs
OCTOBER 14, 2018
A Russian-speaking hacker, who goes by the name of Alexey, claims to have hacked into over 100,000 MikroTik routers with a specific intent, disinfect them. Alexey is a Russian-speaking cyber vigilante that decided to fix the MikroTik routers and he claims to be e system administrator. Pierluigi Paganini.

Security Affairs
JUNE 2, 2020
Security researchers from hacking firm Citadelo disclosed details for a new critical vulnerability in VMware’s Cloud Director platform, tracked as CVE-2020-3956 , that could be abused to takeover corporate servers. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

Security Affairs
MAY 28, 2020
Using a previous version of Exim leaves a system vulnerable to exploitation. System administrators should continually check software versions and update as new versions become available.” Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – APT, hacking).

Security Affairs
OCTOBER 27, 2021
The activity of the Lazarus APT group surged in 2014 and 2015, its members used mostly custom-tailored malware in their attacks. This threat actor has been active since at least 2009, possibly as early as 2007, and it was involved in both cyber espionage campaigns and sabotage activities aimed to destroy data and disrupt systems.
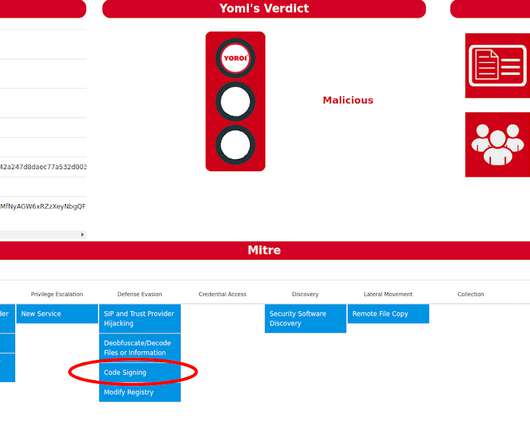
Security Affairs
JANUARY 21, 2020
Many system administrators and companies were rushing to update internet exposed machines, like web servers or gateways, worried about possible remote code execution, reviving the EternalBlue /WannaCry crisis in their mind. . Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.
Security Affairs
OCTOBER 22, 2021
FIN7 hacking group created fake cybersecurity companies to hire experts and involve them in ransomware attacks tricking them of conducting a pentest. The FIN7 hacking group is attempting to enter in the ransomware business and is doing it with an interesting technique. SecurityAffairs – hacking, cyber security).

Security Affairs
MARCH 10, 2020
“They exhibit extensive knowledge of systems administration and common network security misconfigurations, perform thorough reconnaissance, and adapt to what they discover in a compromised network.” ” ~ Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

Security Affairs
JULY 6, 2020
Researchers Rich Warren from NCC Group told ZDNet that hackers are attempting to exploit the flaw to steal administrator passwords from the hacked devices. System administrators need to upgrade to fixed versions ASAP. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

Security Affairs
OCTOBER 25, 2018
Researchers Ron Bowes and Jeff McJunkin of Counter Hack discovered a “high” severity command injection vulnerability, tracked as CVE-2018-15442 , in Cisco Webex Meetings Desktop. ” Cisco advisory reveals that the vulnerability could be exploited remotely by leveraging the operating system remote management tools.

Security Affairs
MARCH 11, 2020
Users and system administrators are recommended to apply the latest security patches as soon as possible to prevent attackers exploiting them. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Copyright (C) 2014 Media.net Advertising FZ-LLC All Rights Reserved -->.

SecureWorld News
APRIL 19, 2021
Being a systems administrator can be a fulfilling job with a lot of rewards. But if you're a SysAdmin for a hacking group, you could be rewarded with time behind bars. This is exactly what is happening to 35-year-old Fedir Hladyr, who was a SysAdmin for the hacking group FIN7.

Security Affairs
AUGUST 19, 2020
Create, start, and terminate a new process and its primary thread Search, read, write, move, and execute files Get and modify file or directory timestamps Change the current directory for a process or file Delete malware and artifacts associated with the malware from the infected system. SecurityAffairs – hacking, BLINDINGCAN).

Security Affairs
AUGUST 19, 2019
Webmin is an open-source web-based interface for system administration for Linux and Unix. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – Webmin, hacking). It allows users using web browsers to set up user accounts, Apache, DNS, file sharing and much more.

Security Affairs
FEBRUARY 10, 2019
“They all come with a default username and “1234” as the default password, which is rarely changed by system administrators.” Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. SecurityAffairs – refrigeration systems, hacking). Pierluigi Paganini.

Security Affairs
OCTOBER 28, 2018
The Center for Internet Security (CIS) has a reference that can help system administrators and security teams establish a benchmark to secure their Docker engine. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Security Affairs – Docker APIs, hacking). Docker Trusted Registry ).

Malwarebytes
APRIL 20, 2021
Ukrainian nationals Dmytro Fedorov, Fedir Hladyr, and Andrii Kolpakov, were members of a prolific hacking group widely known as FIN7. The Carbanak campaign first made international headlines in 2015 as one of the first malware campaigns that specialized in remote ATM robberies. According to acting US Attorney Tessa M.

Security Affairs
NOVEMBER 28, 2018
One month ago, Cisco addressed the CVE-2018-15442 vulnerability, also tracked as WebExec by Counter Hack researchers Ron Bowes and Jeff McJunkin who discovered it. Cisco advisory reveals that the vulnerability could be also exploited remotely by leveraging the operating system remote management tools. and later prior to 33.0.5,

Security Affairs
DECEMBER 11, 2018
“A list of impacted users in those domains is being sent to system administrators, and we will reach out again if any additional impacted users or issues are discovered. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. ” concludes Thacker. .

Security Affairs
SEPTEMBER 2, 2019
Summarizing, crooks extended the list of targets passing from Arm and MIPS-powered devices to Intel systems. . System administrators need to employ security best practices with the systems they manage.” ” ~ Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. Pierluigi Paganini.

Security Affairs
SEPTEMBER 9, 2019
The Windows Background Intelligent Transfer Service (BITS) service is a built-in component of the Microsoft Windows operating system. The BITS service is used by programmers and system administrators to download files from or upload files to HTTP web servers and SMB file shares. ” reads the analysis published by ESET. .

Security Affairs
OCTOBER 17, 2018
In this type of distributed denial of service (DDoS) attack, the malicious traffic generated with the technique is greater than the once associated with the use of memcached, a service that does not require authentication but has been exposed on the internet by inexperienced system administrators. Brasília time, 1:00 p.m.

Security Affairs
NOVEMBER 21, 2019
The Roboto botnet spreads by compromising systems by exploiting the Webmin RCE vulnerability tracked as CVE-2019-15107 to drop its downloader module on Linux servers running vulnerable installs. Webmin is an open-source web-based interface for system administration for Linux and Unix. ” reads the analysis.

Security Affairs
APRIL 23, 2019
Hladyr is suspected to be a system administrator for the group. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. In January 2018 foreign authorities also arrested Fedir Hladyr in Dresden, Germany, he is currently detained in Seattle pending trial. The man is suspected to be a supervisor of the group.
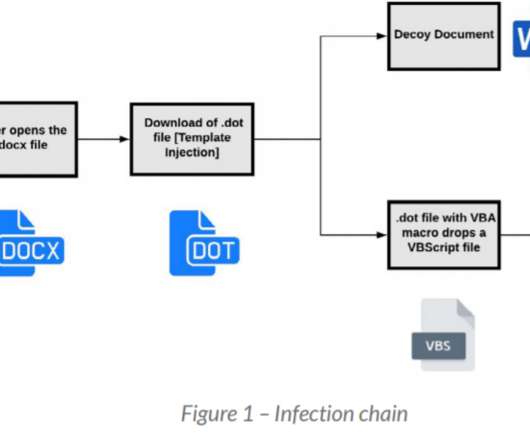
Security Affairs
DECEMBER 7, 2019
US DoJ charged two Russian citizens for deploying the Dridex malware and for their involvement in international bank fraud and computer hacking schemes. 32) and Igor Turashev (38) for distributing the infamous Dridex banking Trojan , and for their involvement in international bank fraud and computer hacking schemes. Pierluigi Paganini.

Security Affairs
APRIL 30, 2020
Furthermore, when planning cloud-based service architectures, corporate system administrators need to evaluate various logging options offered by could service providers and integrate activity log data into existing risk detection flows. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->.

Security Affairs
AUGUST 2, 2018
Three members of the notorious cybercrime gang known as FIN7 and Carbanak have been indicted and charged with 26 felony counts of conspiracy, wire fraud, computer hacking, access device fraud and aggravated identity theft. Hladyr is suspected to be a system administrator for the group. Pierluigi Paganini.

Security Affairs
SEPTEMBER 2, 2018
Administrators may consider using IP-based access control lists (ACLs) to allow only trusted systems to access the affected systems. Administrators can help protect affected systems from external attacks by using a solid firewall strategy. Administrators are advised to monitor affected systems.

Security Affairs
APRIL 23, 2019
Hladyr is suspected to be a system administrator for the group. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. In January 2018 foreign authorities also arrested Fedir Hladyr in Dresden, Germany, he is currently detained in Seattle pending trial. The man is suspected to be a supervisor of the group.

Security Affairs
APRIL 1, 2019
But let’s see what are the execution binaries and what an administrator will see because this analysis IS for rise the system administration awareness: Code execution: execve("/tmp/upgrade""); // to execute upgrade. Copyright (C) 2014-2015 Media.net Advertising FZ-LLC All Rights Reserved -->. O"]); // for persistence.
Security Affairs
DECEMBER 15, 2019
Andrea Pierini (@ decoder_it ) “Andrea is an IT Architect & Security Manager with long-term experience and in-depth knowledge covering all aspects of IT: from SW development to systems administration; networking administration and IT security. He saw and explored almost everything an IT guy could have seen since 1995.

Kali Linux
MARCH 28, 2023
Sana) in August 2015 (at Black Hat USA 15 & DEF CON 23 ). This time, for the first time, people could upgrade their systems between major project updates! Being a system administrator, a patch could contain a security update to stop a vulnerability. As a result, we need to be able to adapt.
Expert insights. Personalized for you.
We have resent the email to
Are you sure you want to cancel your subscriptions?


Let's personalize your content