LeakedSource Owner Quit Ashley Madison a Month Before 2015 Hack
Krebs on Security
JULY 18, 2023
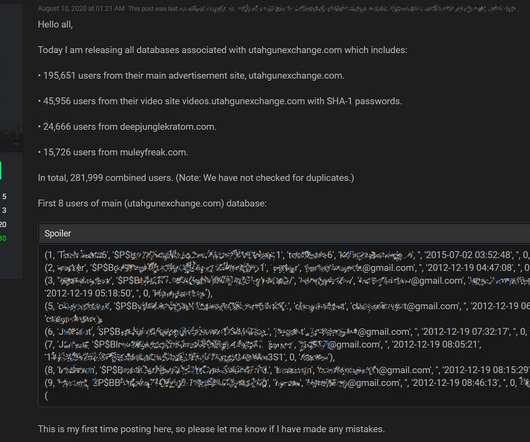
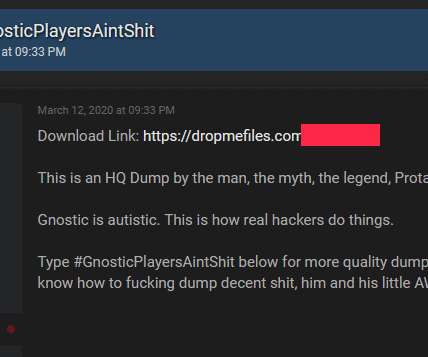
[This is Part III in a series on research conducted for a recent Hulu documentary on the 2015 hack of marital infidelity website AshleyMadison.com.] us , a site unabashedly dedicated to helping people hack email and online gaming accounts. In 2019, a Canadian company called Defiant Tech Inc. Abusewith[.]us








































Let's personalize your content