Xwo Malware scans the Internet for Exposed Services, Default Passwords
Security Affairs
APRIL 5, 2019
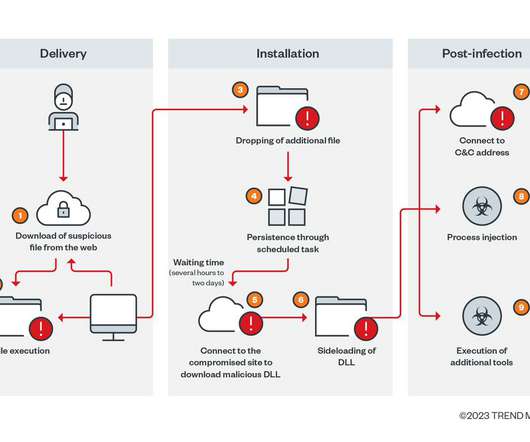
Researchers at AT&T Alien Labs have spotted a malware called Xwo that is actively scanning the Internet for exposed web services and default passwords. Experts at AT&T Alien Labs discovered a new piece of malware called Xwo that is actively scanning the Internet for exposed web services and default passwords.









































Let's personalize your content