StripedFly: Perennially flying under the radar
SecureList
OCTOBER 25, 2023
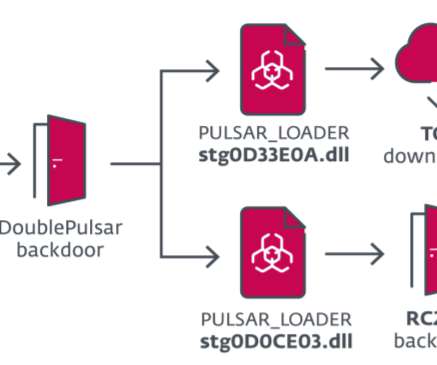
It comes equipped with a built-in TOR network tunnel for communication with command servers, along with update and delivery functionality through trusted services such as GitLab, GitHub, and Bitbucket, all using custom encrypted archives. Subsequent analysis revealed earlier instances of suspicious code dating back to 2017.







































Let's personalize your content