Iran-Linked APT TA450 embeds malicious links in PDF attachments
Security Affairs
MARCH 25, 2024
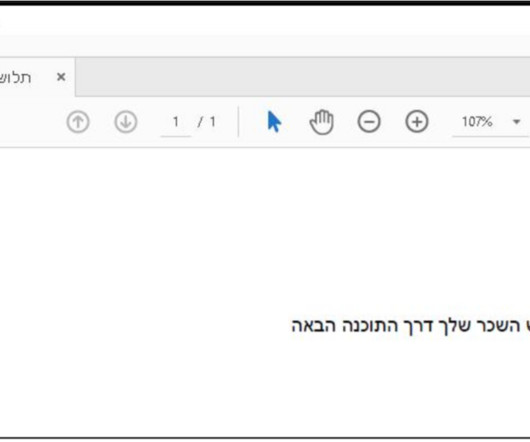
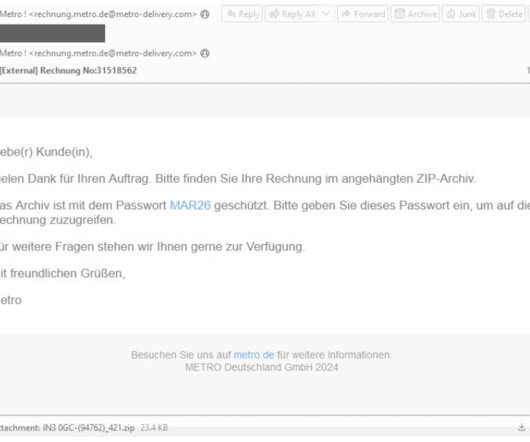
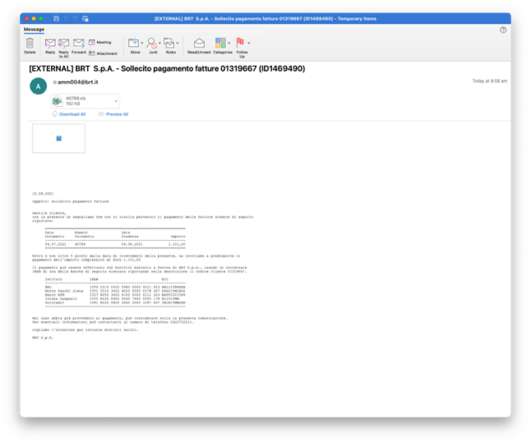
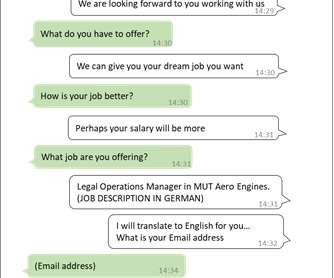
The campaign targeted Israeli employees of large multinational organizations with a pay-related social engineering lure. The first MuddyWater campaign was observed in late 2017, when the APT group targeted entities in the Middle East. The phishing campaign started on March 7 and continued through the week of March 11, 2024.







































Let's personalize your content