Lazarus group uses fake cryptocurrency apps to plant AppleJeus malware
Malwarebytes
DECEMBER 5, 2022
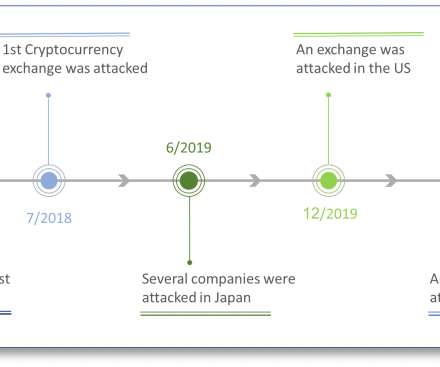
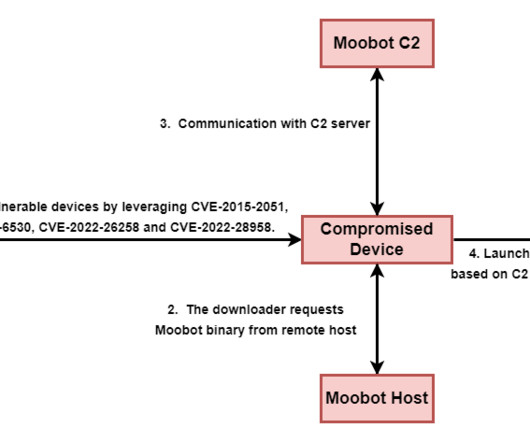
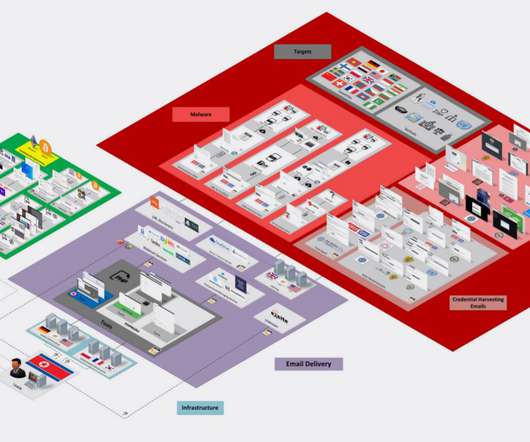
In January of 2022 the Malwarebytes Intelligence Team uncovered a campaign where Lazarus conducted spear phishing attacks weaponized with malicious documents that used a familiar job opportunities theme. One of the group's preferred tactics is to use trojanized cryptocurrency related apps, like AppleJeus. The new campaign. Second wave.












































Let's personalize your content