CVE-2019-0090 flaw affects Intel Chips released in the last 5 years
Security Affairs
MARCH 7, 2020
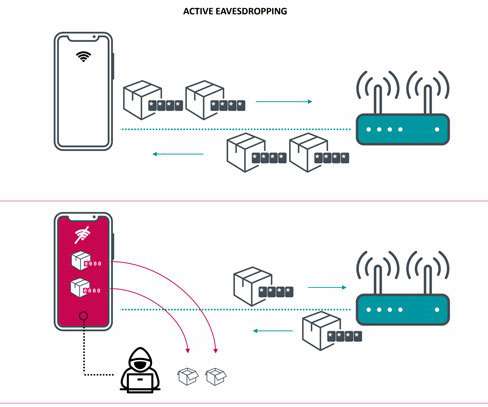
A new vulnerability, tracked as CVE-2019-0090 , affects all Intel chips that could allow attackers to bypass every hardware-enabled security technology. Security experts from Positive Technologies warn of a new vulnerability, tracked as CVE-2019-0090, that affects all Intel processors that were released in the past 5 years.















































Let's personalize your content