Patch Tuesday, December 2019 Edition
Krebs on Security
DECEMBER 10, 2019
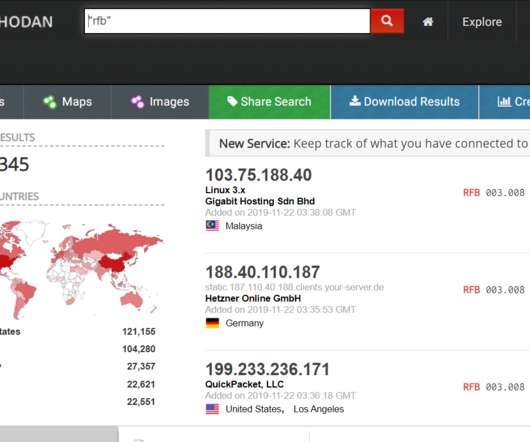
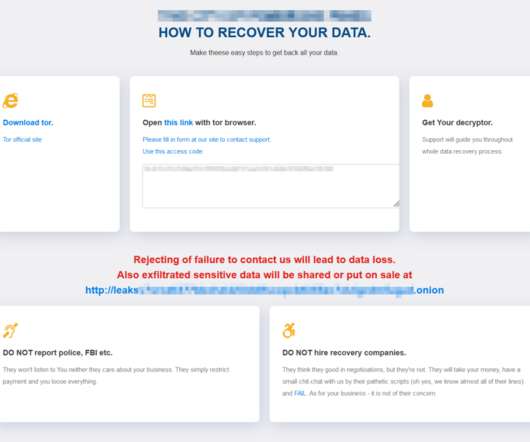
The patches include fixes for seven critical bugs — those that can be exploited by malware or miscreants to take control over a Windows system with no help from users — as well as another flaw in most versions of Windows that is already being exploited in active attacks. It is very likely this is being exploited in the wild.”



































Let's personalize your content