Second-ever UEFI rootkit used in North Korea-themed attacks
Security Affairs
OCTOBER 5, 2020
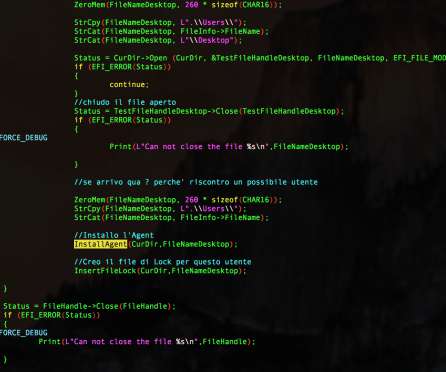
The experts were investigating several suspicious UEFI firmware images when discovered four components, some of which were borrowing the source code a Hacking Team spyware. The firmware malware is based on code associated with HackingTeam’s VectorEDK bootkit, with minor changes. ” concludes the report.















Let's personalize your content