September Firmware Threat Report
Security Boulevard
SEPTEMBER 30, 2021
Spyware found embedded in UEFI and MBR firmware - ran undetected for years. The post September Firmware Threat Report appeared first on Security Boulevard.

Security Boulevard
SEPTEMBER 30, 2021
Spyware found embedded in UEFI and MBR firmware - ran undetected for years. The post September Firmware Threat Report appeared first on Security Boulevard.

Security Affairs
JUNE 7, 2023
June 2023 security update for Android released by Google fixes about fifty flaws, including an Arm Mali GPU bug exploited by surveillance firms in their spyware. The flaw made headlines because it was exploited by surveillance firms for their spyware. This vulnerability grants the attacker system access. In early April, U.S.
This site is protected by reCAPTCHA and the Google Privacy Policy and Terms of Service apply.
Security Affairs
MARCH 29, 2023
Google’s Threat Analysis Group (TAG) discovered several exploit chains targeting Android, iOS, and Chrome to install commercial spyware. The exploit chains were used to install commercial spyware and malicious apps on targets’ devices. The experts pointed out that both campaigns were limited and highly targeted.

Security Affairs
APRIL 3, 2024
CVE-2024-29745 CVE-2024-29748″ The company did not provide details about the attacks, but in the past such kind of bugs was actively exploited by nation-state actors or commercial spyware vendors. The 2024-04-01 security patch level addressed eight high-severity flaws in Framework and System.

WIRED Threat Level
OCTOBER 5, 2020
The tool attacks a device’s UEFI firmware—which makes it especially hard to detect and destroy.
The Hacker News
SEPTEMBER 29, 2021
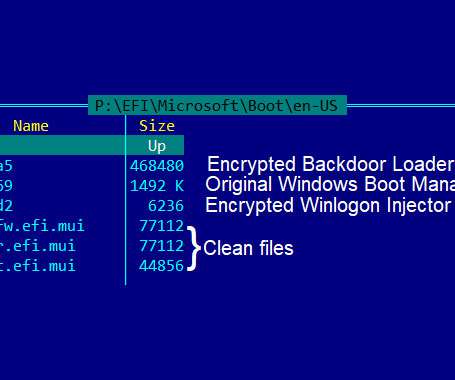
Commercially developed FinFisher surveillanceware has been upgraded to infect Windows devices using a UEFI (Unified Extensible Firmware Interface) bootkit using a trojanized Windows Boot Manager, marking a shift in infection vectors that allow it to elude discovery and analysis.
Security Affairs
OCTOBER 5, 2020
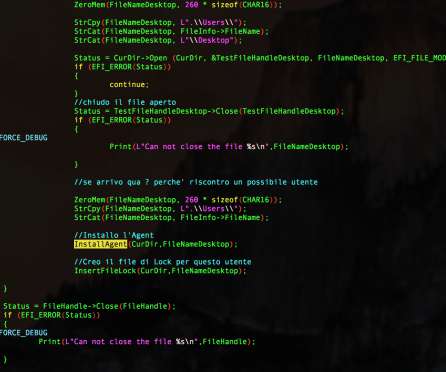
The experts were investigating several suspicious UEFI firmware images when discovered four components, some of which were borrowing the source code a Hacking Team spyware. The firmware malware is based on code associated with HackingTeam’s VectorEDK bootkit, with minor changes. ” concludes the report.
Let's personalize your content