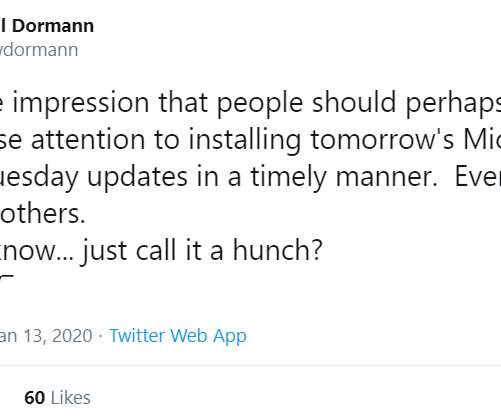
Cryptic Rumblings Ahead of First 2020 Patch Tuesday
Krebs on Security
JANUARY 13, 2020
14, the first Patch Tuesday of 2020. ” The Microsoft CryptoAPI provides services that enable developers to secure Windows-based applications using cryptography, and includes functionality for encrypting and decrypting data using digital certificates. .”










































Let's personalize your content