Hacker leaks passwords for 900+ Pulse Secure VPN enterprise servers
Security Affairs
AUGUST 5, 2020
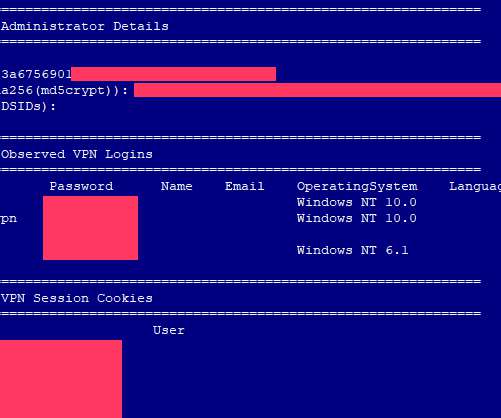
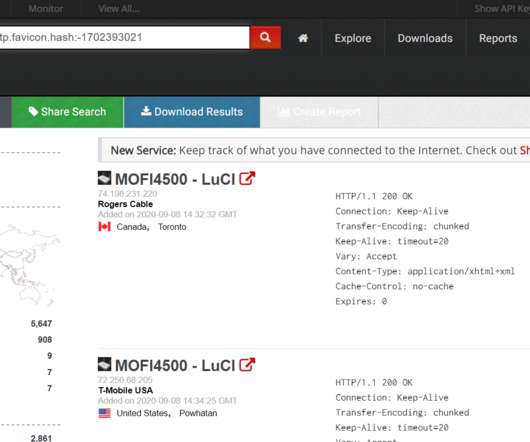
ZDNet reported in exclusive that a list of passwords for 900+ enterprise VPN servers has been shared on a Russian-speaking hacker forum. ZDNet has reported in exclusive that a list of plaintext usernames and passwords for 900 Pulse Secure VPN enterprise servers, along with IP addresses, has been shared on a Russian-speaking hacker forum.













































Let's personalize your content