Credential stuffing cyber attacks targeting home IP addresses
CyberSecurity Insiders
SEPTEMBER 2, 2022
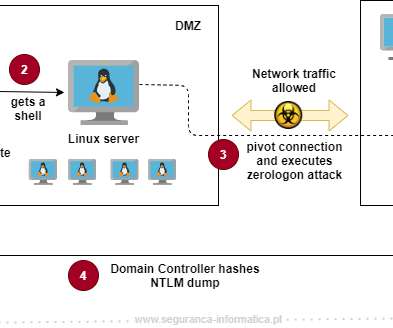
FBI has issued a warning that cybercriminals are hiding credentials on home IP addresses after hacking connected devices like IP cams and routers. To avoid such troubles with passwords, tech companies are coming up with ways to avoid passwords such as 2FA, thus paving the way for password-less authentication environments.










































Let's personalize your content