Cyber Threat by using own name as Password
CyberSecurity Insiders
NOVEMBER 17, 2021
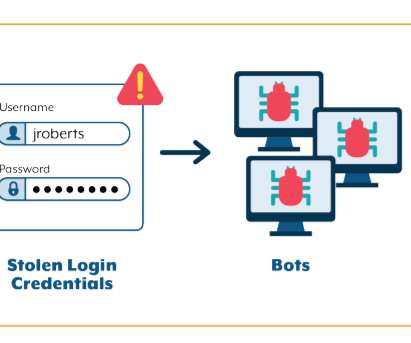
An annual report released by NordPass states that online users are repeatedly committing the same mistake by using their own name as a password, which could put their online identity at a major risk in coming years. The post Cyber Threat by using own name as Password appeared first on Cybersecurity Insiders.














































Let's personalize your content